GROUP3
Contents
Project Title: Music on the net
Group members
- Chris Loubardeas
- Igor Khitrov
- Amanda Kwong
- Annafelle Mendoza
- Raheesa Nazarali
Introduction
In today’s world the Internet is a unique tool which can be used for many purposes from learning to shopping. From CD's to MP3's, music can be stored, shared, recorded, sold, bought and illegally downloaded from the World Wide Web. For some time, downloading music for free in the United States has been illegal; Canada may enact similar laws in the near future as well. However, there are legal ways to use the Internet to purchase music. In our project we will cover the pros and cons of the access to music on the Internet, explore legal and illegal sources of downloading music, as well as other issues relating to music downloads such as the reliability of resources, the possibility of corrupt files and the restriction of the exchange of illegal and non-purchased music through peer-to-peer downloading. Through secondary research we will explore resources to elaborate on music exchanges through the Internet. We will also take a look at various types of programs and sites used to access music on the Internet including iTunes, Limewire, BearShare, and Kazaa. Everyone seems to have their own opinion on this topic; therefore we will discuss our point of view on the issue.
The Beginning
Today almost everyone is aware of and knows how to use the Internet to find and download music, but where did it all begin? In 1999, a young man named Shawn Fanning created a program that he called Napster. Napster was the original peer-to-peer (P2P) file sharing program that opened the door for the Internet into the music industry. Using a centralized database server that stored its clients' personal music information, Napster allowed Internet users to share and swap music files. Since the creation of Napster the concept of music being available on the Internet has flourished to a much larger scale then just one man with one program. Music on the Internet has expanded from P2P's to torrents and along with it has come both beneficial factors and negative outcomes. There has been development in new music file sharing technology, leading to legal issues and a lot of controversy. Now, the online music industry is divided into two groups: a free peer-to-peer service like the old Napster and Limewire, and new programs that charge a small fee for downloads such as iTunes.
Technology
P2P
Downloading music using the Internet requires technology that allows users to do so. There are two main technologies in use today – peer-to-peer music transfers and server-based music downloading. Peer-to-peer (P2P) music transfers work similarly to the sharing of CD’s between friends. Using P2P technology allows users to share music without physically meeting, and in most cases, without even knowing each other. Thousands of users cooperate online to share various files on their computer. These users download special software, such as Limewire, at little or no cost on their computers, which gives them access to the P2P network. Each user in a P2P network acts as a client and a server, as there is no central server. This allows the network share bandwidth, storage space, and computing power equally between users (also called peers). Most modern P2P programs use P2P technology for all purposes, such as searching and downloading. Napster 1.0, a former free P2P program, used a central server to store its clients’ information, but because of this was sued for actively encouraging copyright infringement. Some programs use "supernodes" to run search queries. Users with the most powerful computers and fastest connections are designated as supernodes, which store an index of files of users around him or her. When search queries are run by peers, the search queries search an index from the closest supernode, then move on to more distant supernodes. Supernodes reduce the amount of users a search query must check, greatly increasing search speeds and attain better results.
Torrents
Torrent technology is the latest form of P2P file sharing. Its main advantage lies in its downloading protocols, by downloading many bits of files from different sources simultaneously. This allows download speeds in excess of 1.5Mb per second to be achieved, making large downloads such as full movies possible. Torrents also have an edge over older methods of P2P sharing in its security. Torrents are adware-, spyware-, and advertisement-free. Torrents also filter out corrupted files and make sure that the files contain exactly what they claim. Because torrents rely on multiple sources to achieve large download speeds, many torrent search sites encourage users to allow others to upload their files (seeding), while punishing those who download what they need and not making it available to others (leeching). Because of leeching, connecting to all the peers who have the torrent frequently takes a long time. Still, torrents are slowly pushing out the old ways of P2P file sharing by offering greater security and faster downloads.
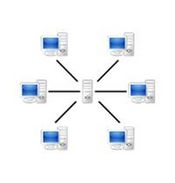
Central Servers
Central servers are used by most music purchasing sites, such as iTunes. These sites use a central server to store information, from which clients can download music files. Most of these structures are legal, and require a payment to be able to download a song. Credit card security becomes a possible security issue, although most sites are very secure.
Legal opposition
U.S.A.
Digital Rights Management
The Digital Rights Management (DRM) was passed to allow copyrighted material to be limited through technological means. For example, a company can use technology to make it so that a CD, can only be copied twice. The DRM was later supported by the World Intellectual Property Organization Copyright Treaty. The treaty was passed in 1996, and was international agreement with over 60 countries participating. The treaty prevents users from producing, making, or distributing technology which overcomes devices under the DRM.
Digital Millennium Copyright Act
The Digital Millennium Copyright Act was signed into law by President Bill Clinton on October 28, 1998, and it amended the previous United States Copyright Act. The act was passed to protect copyrighted music from being downloaded and shared freely through out the internet. The following is a brief summary of what the act declares:
- it's illegal to produce technology that overcomes devices under the DRM
- piracy is a crime
- it's illegal to make, sell or distribute technology that could copy software illegally, however cracking of copyright protection devices can only be used for encryption research, testing computer security systems, and assessing the exchange of information between products
- non-profit libraries and educational institutions liability is limited under certain circumstances
- internet service providers' (ISPs) liability is limited but are expected to remove material on websites which shows signs of copyright infringement
- people who post copyrighted material on the internet must pay licensing fees to the record company
- to copyright material, a recommendation is to be submitted on how to promote education while balancing the rights of copyright owners along with users' needs
- none of the above affect rights, solutions, limitations, or defenses to copyright infringement
If sections of the Digital Millennium Act is broken, the criminal is subjected to fines and the possibility of jail time. The criminal can be charged up to $250,000 and go to jail for up to 3 years. Repeat offenders can pay up to the same amount, but he or she can go to jail for up to 6 years.
Canada
Bill C-60
The United States is more strict when it comes to copyrighted music than in Canada. For example, unlike the United States, Canada does allow file swapping and peer-to-peer networking. However Canada has attempted to become more strict about music sharing and downloading. One of the attempts was Bill C-60, which would have made it illegal to put copyrighted material into file-sharing software (for example BitTorrent), and made it illegal to circumvent copy-protection technology on copyrighted material. Unfortunately, because there was a turn of power in government (2006), the Bill was dropped.
Bill C-61
A new bill has been proposed by the conservatives, Bill C-61. The bill proposed (for the music portion of the bill) would make it so:
- it is illegal to download unprotected music, which could result from $200 - $500 in fines
- it is illegal to copy a CD with a digital lock, and can result in a fine of $20,000
- only one copy of each item per device
- for example someone can copy a song from a CD, but he or she can only have one copy on his or her CD, and one on their computer
Due to the reelection in 2008, the bill has been delayed for discussion, but Stephen Harper (current prime minister of Canada) has said that it will be brought up again. There are many lobby groups that are pressuring the government to pass this bill. The Canadian Recording Industry Association (CRIA) is a lobby group going for the bill. There are also petitions voicing opposition of Bill C-61.
Free vs. Fee
Peer 2 Peer
The creation of Napster in the early 1990's marked the start to free music downloads via P2P networks. P2P networks allowed people the freedom to share any song or music file they had stored on their computer with other users. While many people do not see anything wrong with downloading music for free, it is a violation of copyright laws and record companies and artists are strongly against music being available for free due to lost profits. P2P networks in the United States are illegal and you may be fined; however in Canada P2P networks and downloading free music for personal use are currently legal. Lately, technology has been developing and P2P networks have evolved into faster and more secure networks, and the creation of torrents allowed large files to be transfered in reasonable amounts of time. Torrents are a form of P2P networks. They allow free downloading, but offer faster transfer speeds, safer files, and larger downloads. In the world of free music, the so-called top three programs to use are: Limewire, Aresp2p, and BearShare. Free sites do offer an easy way to access the music at no cost but you risk the threat of downloading malicious software and in some countries breaking the law.
Pay To Play
As music on the net expanded and more people started to steal or download music for free, more legal issues were brought up and an alternative was needed. The solution was simple - make music for sale on the Internet. Programs and sites which charge for downloads became a good alternative to keep music downloads legal by paying royalties to artists and record labels. However just because there was a legitimate and legal way to download music didn't mean it put an end to free music downloading. Currently there are two distinctive types of programs which allow people to purchase music from the Internet. First of you have membership sites which allow users to buy a membership for a set period of time, and during the time period a member can download as much music as they like. Some examples of this type of membership program include Rhapsody music, eMusic, and the new Napster. The other type of program is one in which you can purchase single tracks or albums and only pay for what music you want. In other words you don't buy a membership and download when ever you want. Instead you search their library of music and select either single tracks to purchase for approximately 99 cents, or full albums for $9.99. The most famous pay per song program is iTunes. When you are purchasing music from the Internet, just like anything else there are some issues with security when providing credit card and personal information to make payments.
Credit Card Security
Paypal
- (Leading website in online credit card payments)
How it works
1. The buyer’s sensitive financial information is securely stored on PayPal’s servers.
2. When using PayPal to pay online, the buyer only provides their PayPal email address.
3. The merchants/retailers receive payment from PayPal without ever seeing the buyer’s financial information.
Data Encryption
- The buyer’s computer: When registering on logging onto the PayPal website, PayPal verifies that the internet browser is running Secure Sockets Layer* 3.0 (SSL) or higher. [SSL are cryptographic protocols that provide security and data integrity for communications over TCP/IP networks such as the Internet.]
- In transit: Information is protected by SSL with an encryption key length of 128 bits (the highest level commercially available).
- PayPal Servers: Personal information is stored on PayPal servers and heavily guarded, both physically and electronically. To further shield credit cards and bank numbers, PayPal does not directly connect their firewall-protected servers to the internet.
Lime Wire
- Credit Card & Billing Information: only uses credit card information with to process transactions requested from the Buyer’s User Account
- Encryption Security: Uses Secure Socket Layer (SSL) encryption
- Lime Wire uses IP addresses to analyze trends, track users on the website, and collect broad demographic information to improve Lime Wire and user experience.
- Be aware that static and dynamic IP addresses can be mapped back to users on most ISPs based on the users login time and recorded information.
iTunes:
- Safety Measures: Administrative, technical, and physical measures
- Advises users to change passwords often and use a combination of letters and numbers
- Uses Secure Sockets Layer (SSL) encryption on all web pages where personal information is required
- Buyers must use an SSL-enabled browser such as Safari, Netscape Navigator 3.0 or later, or Internet Explorer
- Uses cookies and other technologies to improve the Apple website
- Gives step by step information to disabling cookies; but will make certain features of the Apple website unavailable.
- All information is stored in a secure database in Cupertino, California, in the United States.
Napster
Online Security
- Uses Secure Sockets Layer (SSL) encryption to protect the transmission of sensitive information
- Stores personal information on a secure server, and uses procedures designed to protect the information Napster collects.
- Commonly uses “session” cookies that only last as long as the user is online; identifies the user as a valid user and ensures no one else can sign on at the same time
- Also uses “persistent” cookies which stay with the user after the session is over and when they are offline; allows to save member name and password the next time the user signs in
- Overall, Napster uses cookies & tracking technology [i.e. Web beacons] within promotional emails or advertisements for Napster. This information is not related to personally identifying customer identification numbers
Overall: All websites claim to use administrative, technical and physical measures to protect a user’s personal and financial information. Most websites that enable the use of credit card payment use Secure Socket Layer (SSL) encryption to protect the transfer of any sensitive financial or personal information. They also employ the use of cookies to collect demographic information; therefore the user should delete their cookies after a session or even disable the use of cookies, with the consequence of disabling certain features of the website. All personal information that is collected by the website is stored in a secure server which is heavily protected.
Pros
There are obviously positives and and negatives with the availability of music on the Internet. Some positives include:
- samples available for preview before downloading
- download individual tracks instead of full albums
- music is easily available to the public
- music is available at cheaper prices; in some cases the music is free
- new bands have a great tool to distribute and showcase their music to people all over the world
- the Internet is a good tool for bands to release music and increase popularity
Cons
Along with all things that have a plus side, there is always a downside. So naturally having music available on the net has some cons:
- copy right infringement issues
- musicians angry that music is available to fans for free
- it is illegal to download freely in the United States
- payment options produce issues with security of credit card and personal information
- some music fanatics download more music than they can possibly listen to; some reports say some people have up to 94 days of music stored on their computers, most of which were downloaded for free
- decreases sales of compact discs, cassette tapes, and records
- downloading of malicious software
Malicious Software
One of the biggest problems today with downloading free music is the possibility of downloading malicious software with the music files. When a P2P network device is installed on a computer it opens a gateway in which malicious software can bypass general security software. If any user downloads a file that has some kind of malicious software, such as a virus or spyware, the malicious software will be leached into the user's computer. A chain reaction occurs because P2P networks connect all of the users' computers; anyone else who uploads the same file will receive the malicious software. So when ever you are involved with P2P networks make sure the files you download look legitimate, and come form legitimate sources. With some programs they will label appropriate song downloads which distinguish safe songs, however it is most often impossible to be one hundred percent sure that a file is safe.
Conclusion
As a group, and as music junkies, we have all used the Internet to access music. Through our informative research we have come to believe that having music available on the Internet is a wonderful thing. We strongly believe that having music on the Internet is the best was to share music to the general public and think that it is a nice way to keep music at low costs. The easy access to music through the Internet has allowed bands to expand their fan base and popularity world wide with ease. There are a few problems such as copyright infringement and the threat of malicious software infiltration, but as a group we believe that music should only be on the Internet as long as there is no illegal or free downloads undermining the artists' profits. Musicians work hard to produce music and people should not be stealing their music for free, and we as a group disagree with the fact that music can be downloaded for free. As for malicious software, people must take precautions before downloading anything from the Internet, not just music. If the files come from a secure site, then receiving malicious software is very unlikely.
References
Chris Loubardeas
- Top 7 digital music services: http://mp3.about.com/od/digitalmusicdelivery/tp/topmusicstores.htm
- Music Pirates: http://www.webupon.com/File-Sharing/Music-Pirates.156147
- The Past, Present, and Future of Downloading music on the internet: http://www.removeadware.com.au/articles/past-present-and-future-of-downloading-music-on-the-internet/
- LimeWire vs. Bit Torrent: File Sharing Comparison: http://hubpages.com/hub/LimeWire_vs_BitTorrent_File_Sharing_Comparison_
- Top 10 Best P2P File Sharing Software: http://technodorm.com/2008/08/17/top-10-best-p2p-file-sharing-software/
- The Dangers of P2P networking: http://www.buzzle.com/articles/the-dangers-of-p2p-networks.html
- The hidden dangers of illegal downloading: http://www.ifpi.org/content/section_news/20080307.html
- A Brief History of Napster: http://iml.jou.ufl.edu/projects/Spring01/Burkhalter/Napster%20history.html
- Pros and Cons of Downloading Music: http://www.buzzle.com/articles/pros-and-cons-of-downloading-music.html
- The Pros and Cons of Sharing Music on the internet: http://www.angelfire.com/de3/jfreeman/termpaper.htm
- Bill image: [1]
- Internet icon image: [2]
- File Sharing image: [3]
- Server based network image: [4]
- Itunes image: [5]
- Limewire image: [6]
- Headphones with Disc image: [7]
- Virus image: [8]
Igor Khitrov
- Advantages of peer-to-peer networks: http://www.solyrich.com/p2p-pros-cons.asp
- About Torrents: http://www.abouttorrents.com/
- Core Concepts in Peer-to-Peer Networking: http://www.idea-group.com/downloads/excerpts/Subramanian01.pdf
- Understanding Peer-to-Peer Networking and File-Sharing: http://www.limewire.com/about/p2p.php
- Study: BitTorrent sees big growth, LimeWire still #1 P2P app: http://arstechnica.com/news.ars/post/20080421-study-bittorren-sees-big-growth-limewire-still-1-p2p-app.html
- File-sharing: http://www.cippic.ca/index.php?page=file-sharing/#faq_peer-to-peer
- How Gnutella Works: http://computer.howstuffworks.com/file-sharing.htm
- P2P: http://www.afterdawn.com/glossary/terms/p2p.cfm
- Bit Torrent File Technology: http://www.articlealley.com/article_16550_45.html
- Supernodes: http://www.kazaa.com/us/help/faq/supernodes.htm
- Is peer-to-peer downloading just digital gluttony?: http://www.nationalpost.com/arts/story.html?id=412792
- Peer-to-peer File Sharing Technology: http://hubpages.com/hub/Peer-to-Peer-File-Sharing-Technology
Amanda Kwong
- Legality in the United States:
- US Copyright Office - Online Service Providers: http://www.copyright.gov/onlinesp/
- The Digital Millennium Copyright Act of 1998: http://www.copyright.gov/legislation/dmca.pdf
- Digital Millennium Copyright Act - Overview: http://www.gseis.ucla.edu/iclp/dmca1.htm
- How Digital Rights Management Works: http://computer.howstuffworks.com/drm.htm
- Protect consumers' digital rights, British MPs urged: http://www.cbc.ca/arts/story/2006/01/17/digital-rights.html
- When is Downloading Music on the Internet Illegal: http://www.webopedia.com/DidYouKnow/Internet/2004/music_downloading.asp
- Legality in Canada:
- Downloading Music: http://www.cbc.ca/news/background/internet/downloading_music.html
- Bill C-61 goes beyond downloading: http://www.queensjournal.ca/story/2008-07-29/news/bill-c-61-goes-beyond-downloading/
- Bill C-61: http://www2.parl.gc.ca/HousePublications/Publication.aspx?Docid=3570473&file=4
- Copyright law could result in police state: http://www.cbc.ca/technology/story/2008/06/12/tech-copyright.html
- Free to file share: http://www.hour.ca/news/news.aspx?iIDArticle=2819
Annafelle Mendoza
- Credit Card Security:
Raheesa Nazarali
- Technology:
- http://netforbeginners.about.com/cs/peersharing/a/aap2p.htm
- http://computer.howstuffworks.com/bittorrent.htm
- http://compnetworking.about.com/od/p2ppeertopeer/a/p2pintroduction_2.htm
- http://netforbeginners.about.com/od/peersharing/a/torrenthandbook.htm
- http://news.bbc.co.uk/2/hi/technology/6544919.stm
- http://www.associatedcontent.com/article/956925/how_torrents_work.html