GROUP 4
Contents
- 1 The Group
- 2 Initial Project Statement
- 3 Background Information
- 4 Is There a Relationship Between Social Networking and Bullying
- 5 How do Bullies Take Advantage of This Technology
- 6 Why has Cyberbullying Prevailed
- 7 What Actions can be Taken to Prevent Cyberbullying
- 8 Implications for Society
- 9 Conclusion
- 10 References
The Group
Group Name: I Dunno's
Members
- Petar Hrkac, Nisha Jeerh, Tony Tran
Initial Project Statement
To Use or to Abuse- Online Social Networking and Cyberbullying
Since its introduction, the Internet has become an integral part of people’s lives. So many people have come to rely on it for many reasons, whether work, education or leisure, that it can almost be considered a necessity of sorts. One of the most common usages of the Internet is for social networking. Realizing this potential, people have created websites that are devoted to this purpose. Through these sites, society can keep in touch with their friends and family, communicate with people sitting next to them or half way across the world, find people they have lost touch with, and express themselves. All they need is access to a computer with an Internet connection.
Despite all the benefits derived from such technology, there are those who find ways to use it to abuse others. It has become common to hear about people who have been harmed, emotionally and psychologically, by others through networking sites like Facebook and MySpace.
Our group is going to explore the impact of social networking sites on bullying in society. We would like to look at the characteristics of these sites that make them appealing to people as a mechanism for bullying, as well as the ways the sites are used as a tool for bullying. In the end we are also going to discuss ways in which this problem could be dealt with.
Background Information
What is social networking
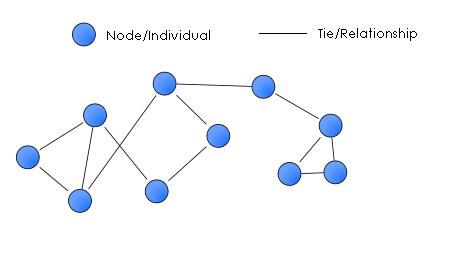
Social networking is one of the largest and fastest growing forms of communication in today's society. A social network can be described as an organized structure of relationships in terms of nodes and ties. A node is scientifically defined as a terminal in a computer network, in other words, nodes are the individuals, groups, and/or communities in a computer network. Ties are the relationships between nodes. For example, two nodes may be related to each other in a social network through a relationship such as a family member, relative, friend, class mate, co-worker, or simply having similar values or beliefs, and common interests. Once a relationship is established between two nodes, they may proceed and start interacting with each other. Depending on which social network you are using and its capabilities, an individual can interact with one another through messaging, chat, e-mailing, pictures, blogs, or posts.NOTE: Nodes/Individuals are responsible for their own actions.
Examples of Social Networking
Social networking through websites Social networking websites are sites that are designed to help you connect and share with the people in your life.[1] Social networking websites are designed for friends who want to talk online, single people who want to meet other singles, families who want to keep in touch, business people and co-workers interested in networking, classmates and study partners, finding long lost friends, and much more! [2]
- MySpace
- Windows Live Spaces
- Friendster
- ..and more!
Social networking through E-mail Social networking can be done through Electronic Mailing. (Also known as E-mail) E-mailing is a store-and-forward method of writing, sending and receiving messages through internet protocol.
- Gmail
- AIM Mail
- Yahoo! Mail
- Windows Live Hotmail
- .. and more!
Social networking through Instant Messaging Instant messaging (IM), consists of sending real-time messages to another internet user. It is a much faster and easier way to communicate compared to e-mail. Since instant messaging allows a user to send messages in real-time, the response time to questions, comments, and remarks are much sooner than some alternative networking services.
- Windows Live Messenger
- Yahoo! Messenger
- Skype
- eBuddy
- ICQ
Social networking through Mobile Devices Mobile devices are one of the quickest and easiest ways to stay connected to the people and world around you. You can socially network through special features such as:
- Phone Calls
- Text Messaging (SMS)
- PIN (Blackberry Instant Messaging Service)
- Multimedia Messaging Service (MMS)
- Receiving e-mails through your mobile device.
Who can Socially Network
Anyone who has a computer and access to the internet can join a social network!
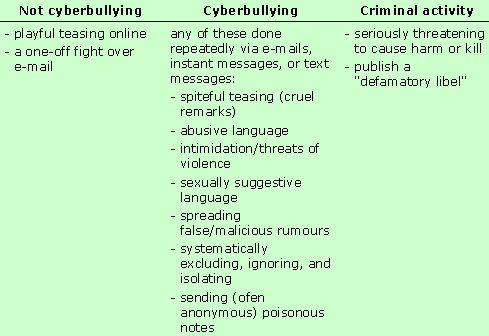
What is Cyberbullying
Cyberbullying involves the use of information and communication technologies to support deliberate, repeated, and hostile behavior by an individual or group, that is intended to harm others [3]. Whether it is direct or indirect, to torment or to tease, between friends, peers or strangers, any intentional action that results in another person being emotionally or mentally abused, including being embarrassed, is considered as bullying. If it is done using some form of communications technology, such as e-mail, cell phones that can send text messages, instant-messaging programs, Internet chat rooms, or web sites or blogs, it is considered cyberbullying. Another criterion for an incident to be considered as bullying is that both the bully and victim have to be minors. If an adult is involved as the initiator or the victim, it is no longer considered bullying, but cyber-harassment or -stalking [4].Though bullying is not a new concept to our society, cyberbullying is especially different from the traditional form in that the individuals involved do not need to be in each others presence for it to occur. It can be initiated from anywhere where there is interactive technology, even the other side of the world! In terms of social networking sites, from any place that has a computer with an internet connection.
The use of technology has made bullying difficult to isolate. It can follow the victims everywhere they go, and can no longer be left at the playground or the mall- it follows them home. As a result, the victims of cyberbullying find it difficult to cope with their lives, when they can no longer feel safe and comfortable at home. Usually the impact is emotional or mental, but sometimes incidents of cyberbullying have progressed to levels where children have killed each other and committed suicide [5].
Who Does it Impact
Everyone!
Cyberbullying impacts everybody in the communities where it occurs, not just the victim.
The Vicitm: For obvious reasons, the greatest effect of cyberbullying is on the people who are targeted, and the results could be devastating, such as a drop in grades, low self-esteem, a change in interests, or depression [6] and even suicide.The Bully: The roles of bully and victim are not static. In fact, research show that the roles are constantly reversing, where the bully becomes the victim and the victim the bully. Also, in addition to the consequences they must face when caught, the psychological well being of the bully must be taken into account, there might be a reason behind their behaviour.
Parents: The effect that cyberbullying has on their children can be devastating to parents, as they watch the psychological turmoil and behavioural changes their children go through. Sometimes they do not recognize the signs of bullying and sometimes they feel helpless to do anything. Parents suffer the most when they do all that they can, but the end result is the death of their child.
Society: Cyberbullying is a social issue. It is always devastating to hear about children and youth who are effected by bullying. Is there something that we should be doing as a society to prevent it? There are a number of organizations devoted to the cause of preventing cyberbullying in society.
Is There a Relationship Between Social Networking and Bullying
Some Statistics
The ways teens respond to cyberbullying:
- 36% asked the bully to stop.
- 34% blocked communication.
- 34% talked to friends about the bullying.
- 29% did nothing about the bullying.
- 28% signed offline.
- Only 11% of teens talked to parents about incidents of cyberbullying.
What they feel:
- Over 50% of teens felt angry after they were cyberbullied.
- Roughly 1/3 of teens felt hurt.
- Almost 15% of teens felt scared.
- Nearly 30% of teens wanted to seek revenge on those who cyberbullied them.
Some Examples
Cyberbullying made headlines when 13 year old Megan Meier committed suicide in her bedroom in October of 2006. Using MySpace, Megan had developed a 'relationship' with someone who she assumed was a new boy in the area. The boy’s name was ‘Josh Evans’. After a while, ‘Josh' suddenly ended the 'relationship', dumping Megan and taunting her. Messages about Megan were sent around and comments posted on MySpace for everyone to see. One of the messages suggested that the world would be better off without her. [9] This devastated Megan and she was unable to understand or cope with what was going on. In the end she took her own life. It turned out that the MySpace account had been made by a family from the neighborhood where Megan lived- the family of a former friend. [10]. Before her suicide, Megan's parents were suspicious of the messages Megan was receiving and had looked into finding out whether it was real or bogus, but the answer they got was that there is nothing you can do. Recently, Lori Drew, the mother of the friend has been found guilty on three counts of gaining unauthorized access to MySpace, but her defense team has already filed an appeal, citing lack of evidence.[11]View an interview by CNN with Megan's parents.
On October 7, 2003, 13 year old Ryan Patrick Halligan committed suicide after being bullied at school and online. Ryan's parents had been aware of him being bullied at school, which was a result other students learning that Ryan was a slow developer, but they did not know what he faced online. After his death, Ryan's father accessed his online accounts and found that in addition to the bullying he faced in school, Ryan had also been taunted and embarrassed online by people he considered to be his friends (one of whom was a bully Ryan befriended). To one of them, he told something embarrassing and funny that happened once and the friend/bully spread the rumor that Ryan must be gay. The rumor and taunting continued into the summer of 2003. During the same summer, Ryan approached a pretty “popular” girl from his school on-line and worked on establishing a relationship with her. When he approached the girl at school, in front of her friends she told him he was just a loser and that she did not want anything to do with him. She said she was only joking on-line. He found out that her friends and her thought it would be funny to make him think she liked him and to get him to say a lot of personal, embarrassing stuff. She copied and pasted their private IM exchanges into ones with her friends. They all had a good laugh at Ryan’s expense.[12] These and much more led Ryan to depression, which he was unable to handle, and Ryan's family was unable to recognize the signs in order to help, until it was too late.
View an interview with Ryan's father, John Halligan.
In October of 2007, students from several Winnipeg schools were suspended due to a Facebook group that was created to bully a teenager with profane and homophobic postings. The group's title included the name of a boy and a very strong vulgarity. The site included two photographs apparently taken with a cell phone camera, of a boy who appeared to be about 13 years old. Many of the students who were making posts were not anonymous- they used their real names, photograph and school name. Some of the students who were suspended felt that teachers should not be allowed to interfere, "teachers shouldn't have the right to do this....it is way to early in the school year to get suspended over something that isn't any of their freakin business," and continued to make vulgar comments, "F--- (boy's name) hes a ----". Yet, there were others who felt he punishment was deserved, "this group is really mean. How would you feel if someone made a group about you like this.....maybe you guys should grow up and not be so irresponsible." [13]
David Knight was a victim of cyberbullying. For years, he had been a victim of bullying at school where he faced teasing, taunting, and punching, but this apparently was not enough. Somebody created a website dedicated to making fun of David. It was called "Welcome to the website that makes fun of Dave Knight" and contained pages of hateful comments directed at David and his family, including lewd, sexual comments. According to David, he was accused of being a pedophile, and of using the date rape drug on little boys. In addition to the website, David received emails such as "You're gay, don't ever talk again, no one likes you, you're immature and dirty, go wash your face." David had no idea who was behind this or why he was targeted. [14]
AND MANY MANY MORE... [15] [16]
The “Kill Kylie” Campaign of Hate and Homophobia
A Fake Facebook Rival
Amanda Marcuson of Birmingham, Michigan
Amy Boucher of Montreal, Quebec
Jodi Plumb of Mansfield, England
Ghyslain Raza of Trois-Rivières, Quebec
Sam Leeson and Bebo [17]
How do Bullies Take Advantage of This Technology
What Characteristics Appeal to the Bully
Many characteristics of cyberbullying appeal to the Bully in ways that traditional bullying cannot. These characteristics include the possibility of the Bully remaining anonymous throughout the ordeal, avoiding virtually all punishment associated with the act of bullying, and the simple of ease of being able to harass and bully someone from virtually anywhere that internet access can be found.Since many online accounts such as emails, Facebook, myspace, etc. require virtually no proof of identity, cyberbullies have the option of remaining anonymous. This allows them to remain "shielded" by the internet, and therefore the fear of the consequences of bullying become erased.[18] The anonymity associated with the internet also allows cyberbullies to act particularly nasty. Many cyberbullies often say and do harsher things that they would do in real life because no one will be able to know or prove it was them. Also, even though email account such as Yahoo and Hotmail can be traced, it is virtually impossible to prove who actually used the account.
As previously mentioned, a vital difference between traditional bullying and cyberbullying is the lack of punishment. At school, a bully is very aware that he or she may be susceptible to punishment by teachers, parents, principals, etc. However, online parents and adults are often quite oblivious to cyberbullying and may have no idea that it is even occuring.[19] This is often due to the fact that children fear that their parents may take away their mobile phone, computer, or internet access. Even if parents and/or teachers become aware of the situation, and possibly even may be able to guess the identity of the cyberbully, the anonymity still disables the possibility of punishment.
The ease of accessing the internet also provides an appealing factor to cyberbullies. No longer does a Bully have to be face-to-face with his victim, or even in the same city for that matter, to be able to harass him.[20] A cyberbully simply has to have some form of connection to the internet, and information about his or her victim's online accounts, such as emails, Facebook, etc. Even if the victim blocks the bully, or deletes him from his/her contact list, a bully can simply create a new account or continue to harassment, knowing the victim very well may hear about it from peers.
Who is Targeted
Firstly, you need to know that you are not alone! Bullies target anyone and everyone! Recall that the objective of a bully is to intentionally harm others. Those who bully generally discriminate differences in an individual because it is the easiest way to make victims feel insecure about themselves. Bullies tend to pick off traits that we have no control over such as our hair and skin color, sex, size, race, etc. DO NOT let these insecurities get the best of you. We were brought into this world and are who we are, that is what makes us unique and special from others. If we learn to love ourselves and become content with who we are, the chances of being a target is significantly lower. [21]
Some Examples of how Social Networking Sites are Used as a Tool for Bullying
Firstly, a cyberbully can create a fake account for their victim. Cyberbullies simply require any active email account to create an account, then they can fill in the details to their desire. Facebook allows for a profile picture to be used, so often cyberbullies can find a picture of their victim to use, making the fake account furthermore convincing. Using the fake account, cyberbullies can add details about their victim, which are ofter untrue and humiliating. These details can include sexual orientation, interests, activities, etc.
Also, a user has the ability of adding photos and "tagging" their friends, essentially linking them to the photos. Cyberbullies can easily PhotoShop a photo to include aspects that will embarrass or humiliate their victim. Commenting is available for photos, so users who see this photo can add input to further embarrass the victim.
Facebook also includes groups and events that can be created. A cyberbully can therefore create an event or group designated to harass their victim. Virtually anyone can be invited or join these groups or events, and there is no way the victim can delete them. For instance, recently "kick a ginger day" occurred on Facebook, discriminating against those with red hair, in which RCMP became involved in. [22]
MySpace, another popular social networking websites today, is also experiencing numerous problems with cyberbullying. For instance, a cyberbully can post their opinions on blogs, a sort of online diary, in which they can post hurtful and humiliating views on others, and even include pictures of their victim for virtually anyone to see. [23]
Cyberbullies can also attempt to hijack and hack into their victim's MySpace account. Once this is done, they have many options of harassment available, including sending messages intended to cause stress or conflict, editing detail's about their victims, etc.
Cyberbullies may also add photos of their victims, much like on Facebook. With the high popularity of built-in cameras on cell phones, cyberbullies may take or obtain embarrassing photos of their victims, and post them online against their will.[24]
Why has Cyberbullying Prevailed
AnonymityUnlike in the real world, cyberbullies do not have to identify themselves online. They can choose and/or make up any identity they want, and use this identity to harass and bully their victims. This aspect of remaining anonymous has allowed for cyberbullies to act virtually however they want. Cyberbullies' reputation can remain completely unaffected thanks to advancements in internet technology.
No Punishment
Cyberbullies are also subject to almost no punishment. This is due to the fact there is no way of confirming the identity of the cyberbully. There is also virtually no way of proving a cyberbully's identity, even is he/she identifies herself online. This is because unless a sort of video surveillance is present, there is virtually no way of saying who was on the computer used to commit the cyberbullying act. This nullifies such strategies as IP-tracking, and allows cyberbullies to hide behind a cushion of safety.
Lack of Awareness
Parents and adults are very unaware of what today's youth's activities on the internet are, and are therefore quite unaware of cyberbullying itself. It is estimated that only about 15% of parents are aware of cyberbullying. [25] Therefore, cyberbullies feel that only their victims and peers will be involved in the incidents, and that parents/adults will not be involved.
Anywhere. Anytime.The crucial difference between traditional bullying and cyberbullying is that cyberbullying can occur from anywhere and at anytime. The cyberbully simply needs to have access to the internet. The cyberbully's victim does not even have to be in the same country as the cyberbully. This also makes it almost impossible for the victim to escape from the cyberbully. In real life, in extreme cases the victim could transfer schools or move to another city. This is not the case in online cyberbullying. Unless the victim gives up online activity altogether, the cyberbully can keep on harassing their victim as long as they still know their contact information.
One Size Fits All
In traditional bullying, although somewhat stereotypical, the bully is often a larger, more physically dominant individual who uses their potential to harm others to and control them with the use of fear. In the online world, this is often not the case. Although cyberbullies often threaten that they are going to cause harm to the victims, a cyberbully can take on any shape or form. Anonymity helps increase this factor. Anyone who wants to bully, simply put, can. This is often very appealing to so-called nerdier or unpopular youth, who may have superior technological skills, creating a sort of "Revenge of the Nerds" effect. [26]
What Actions can be Taken to Prevent Cyberbullying
Children
- Guard your personal information. Never give out personal information online, whether in instant message profiles, chat rooms, blogs, or personal web sites.
- Protect your passwords. Never give them to anyone except your parents. That includes friends.
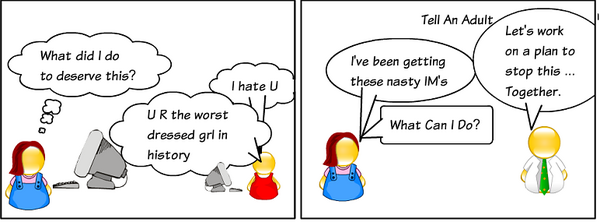
- If someone sends a mean or threatening message, don't respond. For a bully, a reaction constitutes victory. Instead, save the message or print it out and show it to an adult.
- Be aware of who you get messages from. Never open messages from someone you don't know or from someone you know is a bully.
- Don't put anything online that you wouldn't want your classmates to see, even in email.
- Don't send messages when you're angry. Before clicking "Send," ask yourself how you would feel if you received the message.
- Help kids who are bullied online by not joining in and showing bullying messages to an adult.[27]
Parents
- Keep the computer in central location so you can actively monitor your children.
- Supervise your child's online time! Monitoring your child's internet activities can prevent them from going to inappropriate sites or talking to strangers. The internet can be a very powerful communications tool; it is recommended that your supervision is present.
- Tell your children not to open or read e-mails from strangers. In the case of cyberbullying, what you can't read can't hurt you.
- Take advantage of technology: take the time to show your children how to filter or block bad people from their contact lists as well as spend time with your kids online and show an interest in learning.
- Look for signs from your child. Signs may include unusually long hours on the computer, secretive internet activity, falling behind in school, fear of leaving the house, trouble sleeping, and change in attitude and habits. [28]
- Be sure that your children NEVER agree to meet people they meet online. Even people who sound trustworthy and friendly online may turn out to be a cyberbully or predator.
- Have an honest talk with your children. Raise the awareness between yourself and your children with the potential threats in internet activities.
- Protect your children.[29]
- Take an active role in ensuring your child is not the bully!
Schools
- It is important to tell a parent or adult about any cyberbullying incidence as they occur.
- Advise students not to pass along harmful or cruel messages or images
- Train students to avoid opening suspicious e-mails and from unknown senders
- Teach students how to use technology to block or filter communication with cyberbully's.
- Maintain an emotionally safe environment [30]
Creators of the Sites/Internet Service Providers
- Terms & Conditions are set to prevent cyberbullying.
- Privacy settings can allow only your friends to view your profile.
- If you are being bothered by a friend on a social networking site, you can de-friend them. [31]
- Report Abuse to the social network administrators.
- Sites may need to be actively monitored to make sure that it is not being used for bullying
- Any reports of bullying incidents should be given immediate attention
Government/Law Enforcement
- Offer programs to generate awareness and educate
- i-SAFE Inc. is a non-profit foundation whose mission is to educate and empower youth to make their Internet experiences safe and responsible all across 50 states. i-SAFE has been awarded federal funding from the United States Congress to provide students with the awareness and knowledge they need in order to recognize and avoid dangerous, destructive, or unlawful behavior and to respond appropriately. [32]
- Safe to Learn: Embedding Anti-bullying Work in Schools is a program recently launched by UK government. This guidance helps schools recognize what cyberbullying is, and what makes it so different from other forms of bullying. The program also gives a step-by-step outline for schools to prevent cyberbullying and how to respond to incidents appropriately. The program itself is to encourage children, young people and schools to interact electronically in positive manner, and to create and engage in safe communities. [33]
- South Korea has just implemented a new law requiring internet users to provide their real names and social security number that make internet portals responsible for policing message boards and web blogs. This new law ultimately puts an end to anonymity. [34]
- Police Monitor Websites. Cyberbullying is not new and is carefully watched by police. [35]
Technology/Software
Software to help parents protect their children
There is a wide range of products available to parents to choose from, that have been designed with protection in mind. Software such as these are not only great for helping parents protect their children, but also to make sure that their children are not bullies. Privacy issues may arise with the use of such software, so parents need to make sure that they are open with their children, as some may not like being "spied" on. Therefore communication is VERY important!
Spector ProSpector Pro is a very comprehensive Internet monitoring and recording tool. It allows parents to see everything their children do in the exact order they do it with the screen snapshot surveillance recorder; capture every single keystroke typed including user names and passwords; capture and review both sides of a conversation in chats and IMs; read every single email sent and received; review every website visited and what is done on the website, as well as tell if your child is being approached by strangers; see everything done on MySpace and Facebook, including all profiles visited and pictures posted; see every program that is run; be notified when inappropriate language is used or harmful websites visited; block your children from visiting websites or chatting with people you don't want them to. [36]
PC Sentinel Software
PC Sentinel offers software that ranges from just keyloggers to the complete package, depending on what you are looking for. It will allow you to record and monitor websites visited, messages and pictures posted or sent. [37]
CyberPatrolCyberPatrol is a software that allows parents to protect their children from internet dangers. The software helps you understand these dangers, and create restrictions based on what you believe your children can and can't do while using the computer. "With CyberPatrol, you can monitor and manage your children's Internet use in a flexible way that best suits your family…yet allows the freedom to explore safely." CyberPatrol allows your to block harmful websites and images, block downloads, restrict chat and instant messaging, keep offensive language out of chat and instant messenger sessions, limit time spent online, and monitor internet activity. [38]
CyberBully Alert CyberBully Alert software is a tool that allows parents to equip their children with the ability to immediately communicate any incidents of cyberbullying that may occur. A text and email message immediately notifies pre-specified recipients of the online threat. This assures rapid communication between adults and children, and allows children to describe the incident in detail. A copy of the computer screen is immediately documented and stored in a folder for any further investigations. If the threats are harmful and need the attention of authority, this folder can be used to detail the online activity as evidence. All this can happen with a click of a button, when a child feels threatened. [39]
Internet Service Providers (ISPs)/Governments and Law Enforcement
IP tracking
An Internet Protocol (IP) address is a unique number assigned to each computer in a network. Using this unique number, computers in a network can be identified, and therefore tracked to monitor any harmful activities that may be occurring on the internet, such as cyberbullying. Though there are some privacy concerns with IP tracking, the benefits may actually be greater, especially if ISPs notify users that their IP address will be tracked while they are online. Providing sufficient notice to users will allow them to make the choice of whether they want to participate or not, while being monitored. In addition, if ISPs are tracking internet activity, there should be some contract that shows that they will protect the privacy of users, unless they are using the sites for abuse.
The problem with this strategy is that IPs can be assigned either as static or dynamic. Static IPs are one address to a computer and every time the user logs onto the Internet, it has the same address. For dynamic IPs, addresses are randomly assigned from an existing pool of free addresses each time a user logs onto the Internet [40], so the same user may not get the same IP address, making it difficult to track them. In this situation, a good idea may be to watch out for any patterns that may develop in the user's Internet activities.
IP tracking software is also available to the general public on the internet- this could be a possible route for parents and schools to take if they are really concerned about cyberbullying affecting their children, but they should be careful that what they are buying or downloading is the 'real' thing and not some sort of scam or attempt to infect their computers with a virus.
Packet Sniffing
Another possibility for ISPs to aid in tracking cyberbullying is to use packet sniffing. This will allow them to intercept packets of information sent across a network and see everything that happens, including being able to read emails and files sent to individuals. This can help internet service providers and law enforcement to actively monitor where foul play is occurring, and take action accordingly. The information obtained can also be saved to use as proof in the future. [41] If used appropriately, packet sniffing could be a very useful tool to aid in the prevention of cyberbullying.
Once again, it is important to protect the privacy of users, as much more information can be obtained via packet sniffing than may be required, such as credit card information. As a result, ISPs and law enforcement need to be discreet when using packet sniffing strategies as not to completely violate a user's privacy.
Implications for Society
Be AWARE and EDUCATION, EDUCATION, EDUCATION!!!!! This is an issue that needs to be dealt with together- individual effort is not enough. As a community people need to learn to recognize the signs of when cyberbullying is occurring, and need to take action immediately. Some people may feel helpless because the bully cannot be caught or prosecuted, but there is much that can be done for the victims so that the end results are not tragic, as every life is precious. Provide the victims with as much support as possible so that they do not feel that they are not alone. Power comes in numbers. When bullies are no longer effective gaining attention and in reaching their goal of harming others, there is no reason for them to carry on.
Conclusion
Since the increased popularity in social networking sites, many people have been able to interact with each other through instant messaging, sharing pictures and videos, and comments and opinions. Despite the benefits from social networking, this technology has increasingly been used to harm others. Statistics show that 43% of teens have been victimized by cyberbullying in the last year. So what characteristics of social networking sites make it appealing as a mechanism for bullying? This technology is appealing to bullies because they can keep their identity anonymous and are almost subject to no punishment anywhere, anytime. This misused form of communication is a cause for concern to society including parents, schools, and especially victims. In most cases the hands of law enforcement are tied, but there are other methods to prevent victimization on the internet. Some simple techniques parents and schools can use are becoming aware with what cyberbullying is, and learning where and how it occurs, supervising the child's time online to make sure they are not being bullied or bullying, and looking for signs in the children that they are not being victimized. Some things children can do to protect themselves are guarding their personal information and passwords, not being provoked by negative/threatening messages, and discussing bullying incidents with an adult or superior. There is also a wide range of software avauilable that can be used to monitor and restrict internet activities. By raising awareness and becoming more familiar with all aspects of the internet, and specifically online social networking, people can work together to help prevent cyberbullying in society.
References
1) Cyberbullying (November 14, 2008) http://www.cyberbullying.ca/
2) What is cyberbullying, exactly? (November 14, 2008) http://www.stopcyberbullying.org/what_is_cyberbullying_exactly.html
3) Introduction to Cyberbullying (November 16, 2008) http://www.slais.ubc.ca/COURSES/libr500/04-05-wt2/www/D_Jackson/intro.htm
4) List of social networking websites (November 21, 2008) http://en.wikipedia.org/wiki/List_of_social_networking_websites
5) Preventing Cyberbullying: Children (2008, November 24) http://www.slais.ubc.ca/COURSES/libr500/04-05-wt2/www/D_Jackson/prevent.htm
6) Stop Cyberbullying Before it Starts (2008, November 24) http://www.ncpc.org/topics/by-audience/parents/bullying/cyberbullying/cyberbullying.pdf
7) Facebook: Overview (2008, November 25) http://www.facebook.com
8) MySpace: About Us (2008, November 25) http://www.myspace.com/index.cfm?fuseaction=misc.aboutus
9) MySpace Cyberbullying incident produces tragic results (November 27, 2008) http://www.cyberbullyalert.com/blog/2008/08/myspace-cyberbullying-incident-produces-tragic-results/
10) Lori Drew denies MySpace bullying charges (November 27, 2008) http://www.vnunet.com/vnunet/news/2219261/cyberbully-case-kicks-la
11) Drew convicted in MySpace bullying case (November 27, 2008) http://www.vnunet.com/vnunet/news/2231393/drew-convicted-myspace-bullying
12) Megan Meier Parent's interview (November 27, 2008) http://www.youtube.com/watch?v=HFsfDLCkfQU&feature=related
13) In Memory of Ryan Patrick Halligan (November 27, 2008) http://www.ryanpatrickhalligan.org/
14) Interview with Ryan Halligan's father (Novemebr 27, 2008) http://www.pbs.org/wgbh/pages/frontline/video/share.html?s=frol02n3b7q4e
15) The signs of bullying (November 28, 2008) http://www.lockergnome.com/windows/2007/12/07/the-signs-of-cyberbully/
16) 10 ways parents can stop cyberbully (November 28, 2008) http://www.cyberbullyalert.com/blog/2008/07/10-ways-parents-can-help-stop-cyberbullying/
17) 10 ways to prevent cyberbully (November 28, 2008) http://www.hotchalk.com/mydesk/index.php/back-to-school-tips/312-ten-ways-to-prevent-cyberbullying
18) Reporting Abuse (November 28, 2008) http://www.ceop.gov.uk/reportabuse/cyberbullying.asp
19) Stories of cyberbully (November 28, 2008) http://www.cyberbullyalert.com/blog/2008/10/stories-of-cyberbully/
20) cyberbully (November 28, 2008) http://www.cbc.ca/news/background/bullying/cyber_bullying.html
21) Facebook bullies suspended (November 28, 2008) http://www.winnipegfreepress.com/historic/32450209.html
22) Examples of Cyberbullying (November 28, 2008) http://www.slais.ubc.ca/COURSES/libr500/04-05-wt2/www/D_Jackson/examples.htm
23) SpectorSoft (November 29, 2008) http://www.spectorsoft.com/products/SpectorPro_Windows/entry.asp?affil=4
24) PC Sentinel Software (November 29, 2008) http://www.pcsentinelsoftware.com/
25) Packet sniffing (November 29, 2008) http://www.iss.net/security_center/advice/Underground/Hacking/Methods/Technical/Packet_sniffing/default.htm
26) Talk about your troubles ... don't end up like my Sam (November 29, 2008) http://www.thesun.co.uk/sol/homepage/news/article1310516.ece
27) CyberPatrol (November 30,2008) http://www.cyberpatrol.com/_cyberpatrol.asp?gclid=COnHoOXanpcCFRIcawodlmhS-A
28) i-SAFE (December 1, 2008) http://www.isafe.org/
29) UK Government launches Safe to Learn: Cyberbullying Guidance (December 1, 2008) http://eduspaces.net/josiefraser/weblog/196809.html
30) Police Monitor Websites (December 1, 2008) http://educationalissues.suite101.com/article.cfm/police_monitor_websites
31) The Internet: A vast network of networks (December 3, 2008) http://pages.cpsc.ucalgary.ca/~tamj/203/topics/internet.html
32) CyberBully Alert (December 3, 2008) http://cyberbullyalert.com/index.php
33) CyberBullying.ca (December 5, 2008) http://www.cyberbullying.ca/
34) What is cyberbullying? (December 5, 2008) http://74.125.95.104/search?q=cache:fonjUM-dPRsJ:www.cyberbullying.ca/pdf/Cyberbullying_Information.pdf+cyber+bullying&hl=en&ct=clnk&cd=2&gl=ca&client=firefox-a
35) RCMP probe BC teen for Facebook "kick a ginger" forum (December 5, 2008) http://www.theglobeandmail.com/servlet/Page/document/v5/content/subscribe?user_URL=http://www.theglobeandmail.com%2Fservlet%2Fstory%2FLAC.20081122.REDHEAD22%2FTPStory%2FNational&ord=15863969&brand=theglobeandmail&force_login=true
36) A Cyber Bullying Primer (December 5, 2008) http://social-networking-tagging.suite101.com/article.cfm/a_cyber_bullying_primer
37) The Power Hungry and Revenge of the Nerds (December 5, 2008) http://www.stopcyberbullying.org/parents/howdoyouhandleacyberbully.html