Group 3 T35 Tingxi Tan -Bluetooth
Contents
Team Members
- Joseph Girgis
- Alex Burk
- Evann Neumann
Argument
This Wikipedia will look into the aspects to decide whether Bluetooth is worthy of a purchase by the common citizen. By looking into the Pros and Cons, it will be easy to weigh out the difference and see how reliable Bluetooth can be. We will see how safe Bluetooth is and how convenient it is.
Bluetooth Introduction
Bluetooth was invented in the year 1998 to help get rid of the mass of wires that surround a computer, and more recently cell phones in a fast and efficient manner. Bluetooth connection is wireless and automatic after the first connection has been set-up and established. Bluetooth wireless technology is geared towards voice and data applications. Bluetooth uses short-range radio frequency to connect the objects that it is connecting. Some major features of Bluetooth wireless technology are robustness, low power, and alongside, its low cost. Many features of the core specification are optional, allowing subtle differences in each individual product. Bluetooth wireless specification was designed to enable cable-free connections between:- Computers
- Mobile phones/Headsets
- PDA's
- Printers
The Nintendo Wii and Playstation 3 also uses Bluetooth for their wireless controllers for the console. Bluetooth in these devices is named after a king named Harald "Bluetooth" Gormson.
Bluetooth devices are recorded under 3 classes: Class 1, Class 2, and finally, Class 3. These devices are classified under their Maximum Output and their Power.
- Class 1 has a maximum output of 100 mW (milliwatts)and a power of 20 dBm (decibel per milliwatt)
- Class 2 has a maximum output of 2.5 mW and 4 dBm
- Class 3 has a maximum output of 1.0 mW and 0 dBm
Class 2 is the most common class found in cellular phones.
There has been a long list of history with Bluetooth dealing with its upgrades and numerous counts of hacking and infections with the Bluetooth technology.
History
Bluetooth was developed by the Bluetooth Special Interest Group (SIG). This group includes some of the biggest names in Industrial Automation, Automotive, computing, Telecommunications and network industries; and was founded in September of 1998. Some of the biggest names in this group include Microsoft, Agere, Motorola, IBM, Ericsson, Intel, Toshiba and Nokia, and thousands of other Associate and Adopter companies, one of which is SP Commerce LLC. The name "Bluetooth" was originally used as a code name by the developers, but the name stuck. It was taken from the name of a 10th century Danish King Harald Blatand (Loosely translated to Bluetooth). King Bluetooth was influential in uniting Scandinavian Europe. This was during the era of wars and feuding clans which had torn apart the country.The Bluetooth SIG thought that this name was fitting for two reasons, first off: Bluetooth technology was developed in Scandinavia, and 2: Bluetooth technology was invented to unite technologies all over the world, like cellphones, automotive and computing markets. Bluetooth technology combines various forms of wireless communication and unites them into one low-cost, low-power, secure and globally available radio frequency.
The Bluetooth logo is also keeping in line with this history, it is a unification of the runic symbols for "H" which looks similar to an asterisk and "B", which are the initials for Harald Bluetooth. This logo was released at the same time that the SIG was formally released to the public.
After the beginning of Bluetooth in 1998, there have been major upgrades that have begun, starting in 2003. The main concern in 2003 was the security problems which was due to the poor implementation of Bluetooth.
2004 found itself with the first virus used on Bluetooth to spread the virus to other mobile phones. It was discovered by the anti-virus company known as Kaspersky. However, the virus was only regarded as a potential risk and not a serious one. In 2004, Bluetooth Version 2.0 was announced but not implemented yet.
In the beginning of 2005, a malware worm found on mobile phones began targeting phones using Bluetooth enabled devices to duplicate itself. This worm rendered mobile devices unstable to use when it has infected the file sent to the mobile. The file was called "velasco.sis". Also in 2005, a paper was published to describe methods for obtaining the PIN for a Bluetooth device. In August, police in England issued warnings about hackers using Bluetooth to find the location of other devices who use Bluetooth left in cars. This lead to the thieving of such devices. People were advised to deactivate Bluetooth when they are not using these devices. 2005 brought forth the successful Bluetooth Version 2.0 that was announced in 2004.
Researchers in 2006 had found that with so many devices left in a visible state will lead to a huge spread of a future Bluetooth Worm.
2007 brought forth demonstrations on the first Bluetooth PIN cracks.
"Analysts predict that by the year 2012 one-third of all new cars will have built-in Bluetooth connections"
Pros
Bluetooth is a very convenient addition to many devices that is becoming more common by the years. A lot of functions that the Bluetooth products have would be it's ability to exchange ringtones, wallpapers, and business cards with its wireless nature with other people who use the product. You may use the wireless headset while driving a car, which is convenient for busy drivers. This reason makes driving much more safer than having one hand on a device such as a cellular phone. Being able to use Bluetooth as a computer speaker and microphone as an audio gate is also possible.Bluetooth is also well known for consuming very little battery power while in use which is favorable to small gadgets which have a short battery life.
What seems to bring in Bluetooth customers is the key fact that the Bluetooth SIG (Special Interest Group) releases new products every few days.
The Bluetooth headset is a very convenient use of communication to those who are disabled, in wheelchairs or not capable of using their arms to use another communicating device such as a cell phone. For the people who are capable of body function may simply use a Bluetooth headset to listen to music. This will also allow them to easily hear if someone is calling, and with a click of a button they are able to switch to communication with the person who had called. It is very convenient for business people as well if there are lots of calls to be answered on a regular basis.
Aside from the headset, Bluetooth can be used to pair your cellular phone to a computer. By entering the appropriate password that protects the Bluetooth enabled cellular phone, you can enable your cellular phone to dial your ISP (Internet Server Provider) and connect to the internet by clicking on "Bluetooth Modem --> Connect" from the Bluetooth menu. When you have Bluetooth enabled on your computer, a quite of bit of options become available again between the computer and a mobile phone. While Bluetooth is on, your computer can perform a file transfer or synchronization with the mobile phone very easily.
While a big problem before, the Bluetooth SIG is always upgrading their products to protect users from serious hackers and computer viruses. See the following section for further detail on hackers and viruses. Once the Bluetooth SIG has discovered that their product is vulnerable to hacking in 2003, they decided to upgrade their technology as often as possible due to the first version (Version 1.0) had many problems and restraints. Bluetooth Version 1.1 was designed to correct all the problems and restraints Version 1.0 had. This was considered the most successful upgrade. Following 1.1 came Version 1.2 which reduced radio interference, better quality for audio connections, and enabled devices to send at a faster transmission rate. Bluetooth Version 2.0 further added more functions to any device that was capable of using Bluetooth. Version 2.0 allowed transmission speeds to increase to three to ten times as fast as the previous versions. The power consumption was also lowered significantly from this upgrade. It supported multicast and broadcasts. This most recent Bluetooth upgrade is much more convenient to people and makes the device a much bigger success in the history of it's development. With Version 2.0, the ability to use wireless video game controllers have become possible starting with the Playstation 3.
Medical equipment have began adding Bluetooth into their device by numerous hospitals to enhance medical care for patients.
Cons
Despite the fact that the Bluetooth has many excellent qualities about it, there is also quite a few qualities that make Bluetooth difficult to use, and possibly extremely unsafe with its security.
To start off, the initial connection setup used to activate Bluetooth is quite complicated and difficult for many to set up. For starters, upon purchasing the Bluetooth device, the default factory setting has the Bluetooth radio initially turned off, so the user must manually turn it on and let it be open to other viewable members while assigning it a public name. Users will then have to exchange a passkey before prompting the new connection. The passkey is a number that allows your device to associate with another device that has Bluetooth enabled. This is to assure you have security to protect your device. This will only let your computer to safely connect to the device you want to connect to and not accidentally connect to another device that may just happen to be close. It is advisable to use a long passkey to be more secure when connecting. Because of this, many users forget their password due to the length which is quite inconvenient to the user.
Bluetooth can also be inconvenient to other citizens who are unaware of the small Bluetooth headset another person may be wearing. This could lead to misleading communication when one person may try to talk to another one and get an awkward response due to the Bluetooth user speaking to someone else on what could be a tiny Bluetooth headset.
Bluetooth also sparks up some health concerns due to the radio frequency. However, Class 1 Bluetooth has the same frequency as a normal cellular phone while both Class 2 and 3 have a much lower maximum power output making them much safer. They are considered much safer with less concern for a health hazard as a Class 1 device would have. Luckily, however, Class 2 is the most common class found in a mobile phone.
What can be one of the worst aspects of Bluetooth is its security issues. Bluetooth is becoming more of a basic feature on a cell phone and many people have been misusing the technology, enabling them to hack into other peoples phones via Bluetooth. If the Bluetooth device (such as a cellphone or computer) is insecure, there can be intrusion to their personal privacy and data. There are generally three categories of hacking with Bluetooth:
Bluejacking
The easiest of the four different types of hacking. The hacker simply uses Bluetooth to send phone contacts or advertisements to a nearby phone that has Bluetooth enabled. It is equivalent to spam on the internet since it is both unwanted and takes advantage of wireless communication. This kind of hacking is generally harmless compared to the other two types.
Bluesnarfing
The second type of hacking. Unlike Bluejacking, Bluesnarfing goes the extra distance to gain access to data from the victims device. Messages, contact numbers, pictures, and calendar events are only a few types of data that may be stolen. This is achieved by bypassing the usual pairing requirement, as entering the passkey to make a connection between the two devices. In even worse cases, the hacker may even find and hack into devices that the user has set on to invisible to random Bluetooth users.
Bluebugging
As if the offender had physical access to the Bluetooth device, the hacker is able to form commands for the device to perform. The hacker may then make phone calls through the victims phone, send text messages with the phone, and even eavesdrop into conversations that involve the phone that they forced access into. The victim is also able to be receiving a Trojan/Virus as if it was a computer. Because Bluebugging can be done through the use of laptops, the situation is even worse when the hacker is able to send actual Trojans and Viruses to the victims device.
Luckily, to save yourself the grief of having to deal with people who decide to hack into Bluetooth devices, all you have to do is upgrade to the latest available patch to get rid of these vulnerabilities. Do not connect to any device that are unknown to you at any times. And simply, you can just turn off the Bluetooth application when it's not in use.
As well, be aware that it is safer to use and connect to other Bluetooth devices in the safety of your own home. Failure to do so can lead to an easier time for malicious users to crack your PIN code when they see a pairing device out in the public.
Statistics
When Bluetooth was first released in 1998, there was over 3400 companies that were part of the Bluetooth Special Interest Group.
Before 2003, 125 million Bluetooth products were sold. This number doubled from 2003 to 2004 raising the number to 250 million units sold. The growth in units sold doubled once more from 2004 to 500 million units.
On May 30, 2005, the Bluetooth SIG team had announced that they were shipping $5,000,000 (5 million) Bluetooth units on a weekly basis to meet with the high consumer demand. This shows the acceptance of Bluetooth technology as a common utility.
Over 100 manufacturers in Taiwan were expected to produce in excess over 46 million Bluetooth units in the year 2005 which was 79% higher than the previous year in 2004. Hong Kong had manufactured 5.1 million units in 2005 which was 135% more than 2004. There was an anticipated growth of 125% through out China making 3.3 million Bluetooth units in 2005.
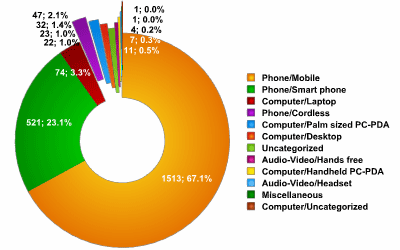
This above image shows the percentage of the amount of devices using Bluetooth in 2006. We see here that Bluetooth is used mostly for Mobile Phones (67.1%), Smart Phones(23.1%), Laptops (3.3%), and Cordless Phones (2.1%). The rest of the percentage falls under palm sized PDA's and Headsets
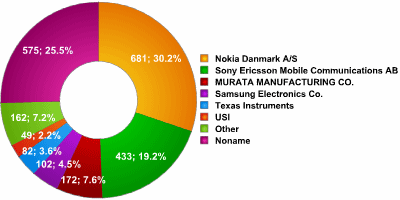
This image shown above illustrates the amount of participation demonstrated by 35 main companies that are apart of the Bluetooth SIG in the year 2006. Though there are 35, only 6 individual companies carry the bulk of being part of the SIG. Nokia appears to be the most active participant at 30.2%, and going clockwise, we see Sony Ericsson at 19.2%, Murata Manufacturing at 7.6%, Samsung Electronics at 4.5% followed by Texas Instruments and USI at 3.6 and 2.2% respectively. The remainder of the companies are either barely known companies, or no name companies.
Conclusion
Despite that Bluetooth has a fair amount of Pros and Cons, we can safely say that Bluetooth is most definitely worthy of a function to have for anyone.
- It is an efficient method of communication for those who are disabled and for the business people. The common people can use the Bluetooth technology to efficiently send files and messages to other Bluetooth users and the headset is a very convenient for the common folk.
- Bluetooth is also fairly inexpensive for what it is. It is affordable to everyone who is able to afford a mobile phone. It is wireless and takes away the inconvenience of wires and cords.
- Bluetooth has the property of interoperability. This allows Bluetooth devices to connect to other devices that are of different models.
- Bluetooth has next to zero radio interference due to the SIG team constantly upgrading its performances with its low power signals and frequency hopping. Alongside with low power signals, this only means that there is low energy consumption which is great when implemented into cellular phones.
- The service is constantly upgraded due to the devoted Special Interest Group.
- Between Bluetooth devices, you can send Voice and File data fast and efficiently.
- Regardless of the many security scares, the hacking and virus part of the Bluetooth technology is blown out of proportion. There are a lot of upgrades to fight against new ways of hacking. Hacking Bluetooth is becoming much harder by the upgrade, taking away the motivation from casual hackers.
- There are 3 different kinds of security mode between paired devices to protect the devices
- Security Mode 1: non-secure
- Security Mode 2: service level enforced security
- Security Mode 3: link level enforced security
References
The website references for this groups members:
Joseph Girgis
http://www.bluetooth.com/Bluetooth/Technology/Works/
http://web.archive.org/web/20060519034246/www.niksula.hut.fi/~jiitv/bluesec.html
http://www.bluejackq.com/what-is-bluejacking.shtml
http://www.thebunker.net/resources/bluetooth
http://www.bluetooth.com/Bluetooth/SIG/
http://hubpages.com/hub/Types-Of-Bluetooth-Hacks-And-Its-Security-Issues
http://www.wirelessdevnet.com/channels/bluetooth/features/bluetooth.html
http://www.dancewithshadows.com/tech/bluetooth-market-shipments-statistics.asp
http://www.viruslist.com/en/analysis?pubid=188833782
http://ddp3532bluetooth.wordpress.com/security-issue/
http://www.auto123.com/en/news/car-news/what-is-bluetooth?artid=101916
http://www.trendmicro.com/vinfo/secadvisories/default6.asp?VName=Bluebug
Alex Burk
http://www.bluetomorrow.com/content/section/11/38/
Evann Neumann
http://blog.justindorfman.com/2008/03/how-bluetooth-got-its-name-in-nut-shell.html http://dotsep-wireless.blogspot.com/2007/01/origin-of-bluetooth.html