T17 Group5
Contents
Team Information
Team name: MGD!
Team Members:
Clark
Orza
Sproule
Yi
Technology
Hacktivism
Issue
What is the impact of hacktivism on the world?
Introduction
The technological revolution has brought about massive changes in the way modern humans live their lives. Technology has infiltrated nearly every aspect of our lives, with the internet at the forefront of the invasion.
In this age of information and advancement, two distinct groups have coalesced into one to take advantage of the new tools available: hackers and activists. The hybrid-child of these two is called "hacktivism", and those who practice it have been making waves throughout the world through the use of their combined skills in political demonstration and technical savvy.
This report will explore the world of the hacktivist. Among the topics discussed will be the history of hacktivism, hacktivist ideals, notable incidents, and the trends appearing in hacktivist communities today.
In the end, one question will be answered:
What is the effect of hacktivism on the world today?
What Is Hacktivism?
Even amongst hacktivists themselves, hacktivism is hard to define. What some would deem "hacktivism", others would identify as simple website defacement or internet vandalism. The general consensus on what separates "hacking" incidents from "hacktivist" acts is the political element.
Perhaps a good place to begin looking for the true nature of hacktivism is from the hacktivists themselves. TheHacktivist.com defines it as "the writing of code or manipulation of code to promote or convey a political ideology", which appears to be a surprisingly unbiased definition. More passionate parameters are set by Oxblood Ruffin, the leader of the hacktivist group "Hacktivismo": "Hacktivism forges conscience with technology and girds us against the disagreeable nature of conflict. It allows us to mount better arguments, rally unseen allies, and take on any tyranny."Essentially, hacktivism is the combination of "hacking" and "activism", in which the techniques traditionally employed by hackers are used to convey a political ideology or spread a political message. The use of the internet allows this to be done on an immense scale, where conventional activists are confined to their targeted geographical area, except in cases where media coverage spreads the message beyond this.
Hacktivist Beliefs
In the same vein as the hybrid name, the beliefs of the hacktivist are an amalgamation of both hacker and activist ideals. They are cyberlibertarians, believing strongly in the dissemination of information to the public. This can be seen in the Hacker's Tenet (a code followed by hackers), in which the second rule is that "[a]ll information should be free". They distrust authority and advocate decentralization of power. Additionally, hacker society is not based on age, race, religion, sex or rank outside of the internet community. Rather, it is based on hacking skill and infamy.
These hacker beliefs are fused with the beliefs of the activist, which are generally anti-war and anti-violence. They believe in the fight against violence and injustice through the spread of information.
Techniques and Case Studies
Hacktivists employ a number of techniques to obtain their goals, many of which involve spreading information or placing it in strategic (read: visible) places.
The most common of these is defacement, in which a website is cracked into and altered to convey a message. Denial of Service (DoS) attacks are also common, and involve hacktivists barring people from accessing websites or services. Virtual sit-ins are a similar method, in which websites are accessed repeatedly or simultaneously en-mass, causing delays or an entire website crash. Hacktivists continue to develop new coding techniques and technologies to accomplish their goals.
Although defacement has been around since the dawn of hacking, the release of Microsoft's IIS Server caused an enormous spike in the number of website defacements due to massive security gaps in the system. This is known as the Unicode Directory Transversal Vulnerability, and it allowed even weak or inexperienced hackers to access servers and change websites.
Milw0rm Case StudyOne of the earliest cases of hacktivism is that of Milw0rm. Three teenagers hacked into the Bhabha Atomic Research Centre in Bombay, India in order to protest the testing of nuclear weapons. They “altered the homepage, stole emails that were exchanged among nuclear scientists before and after testing and erased all the data on two of BARC’s servers” (Crackers: We Stole Nuke Data, 1998). It was a non-violent protest designed to disseminate information and draw attention to the nuclear weapons testing that was being conducted. Beyond that, they may have managed to actually hinder the testing due to the loss of data on the two servers.
While their intentions may have been noble, these hacktivists obviously broke laws and may have done serious damage and wasted a lot of money put into the atomic research that was being done. Depending on your point of view, this case could have been a total disaster or a serious blow in the name of justice.
Mawanella Case Study
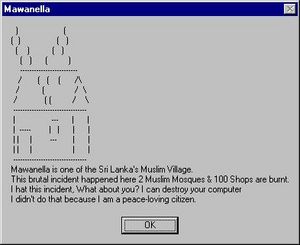
A different form of hacktivism can be evidenced in the Mawanella worm case. Here, an email virus was received by an internet user with the title "Mawanella". Once opened, the otherwise harmless virus accessed the user's contact list and sent itself to everyone listed. This method is incredibly efficient in information dissemination as it quickly spiderwebs outward from the first person to receive it, eventually reaching people on all corners of the globe.
The information being conveyed concerned an incident in Mawanella, Sri Lanka where two Muslim mosques and over 100 shops were burnt to the ground. The message in the email relayed this incident and closed with "I can destroy your computer I didn't do that because I am a peace-loving citizen" (Sri Lankan virus spreads political message, 2001).
This is hacktivism at its most pure and easily-defended, as the virus did nothing to the computers of the users it went through besides sending itself to other computers. It was simply a means of spreading information, rather than doing damage.Sarah Palin Case Study
More recently, during the 2008 Presidential Campaign in the United States, hacktivists attacked prospective vice-president Sarah Palin by cracking her private Yahoo! email account and posting screenshots and messages from inside on the website Wikileaks. The hacktivists--part of a group called "Anonymous"--claimed to have done it to expose the fact that Palin had been conducting official business through her private email instead of her house email. The group came under severe attack when it was revealed that her actions were totally legal and, in fact, necessary as certain subjects cannot be discussed through her official email account due to the public nature of that account.
Here we see hacktivism that is quite arguably misled and could have had a large number of damaging effects depending on the information that was leaked. The hacktivists obviously broke privacy laws through these actions, and were unaware of the legal nature of Palin's actions.
Positives and Negatives
While hacktivists are often seen as criminals because of the vandal-like nature of many of their crimes, there are still two sides to every story.
Arguably the best thing about hacktivism is its non-violent nature. Through this tool protests cannot go awry and end in the death of protesters or police. Injury and death are virtually impossible. Hacktivism can also draw attention to incidents or situations that may require intervention by an official entity because of information leaks. Additionally, while website defacement and the like can have reprocussions, demonstrations such as these are a welcome respite from real-world terrorist attacks and extremist protests.
Despite these pros, the cons of hacktivism are plentiful. Hacktivist communities could potentially bring together extremists who believe in real-world action rather than non-violent online action. The dissemination of private information is also potentially dangerous, as the leaking of phone numbers, street addresses, full names and other such records could easily be gathered and used for a whole slew of illegal activities once given to the public. Website defacement, DoS attacks and other such methods are also a violation of the rights of those who created and manage the websites.
What it comes right down to is opinion. There are pros and cons to hacktivism--those whose beliefs align with the hacktivists may rally behind them, while those targeted by the attacks will stand vehemently against. Hacktivism poses the same question as real-world activism: who is in the right?
Evolving Hacktivism
Within recent years, hacktivism has gained more negative attention than positive. This is, in large part, due to the formation of hacktivist groups forming and beginning to compete with each other. This can be seen in the case of the MHC (Muslim Hackers Club) versus the PHC (Pakistani Hackers Club), who have started a cyberwar against each other that has affected even the Pakistani and Indian government websites.
This is a movement away from actual hacktivism, as political drive is no longer the main factor in the hackers' actions. Rather, the groups compete for a higher position in the hacking hierarchy, corrupting the initial ideals of the hacktivist which deal with information dissemination and the spread of political messages.
At the same time, true hacktivism has stayed strong. One only has to look at the Sarah Palin case to see that hacktivists everywhere are standing up for their beliefs in freedom of information.
Conclusion
Hacktivism has effected our world whether we know it or not. Vast amounts of leaked information have been spread via the internet because of hacktivists, and anyone who spends any amount of time surfing the web has probably come across at least a tidbit of knowledge bestowed upon the world by an ambitious hacker-activist hybrid.
It remains an effective and efficient means of spreading information and expressing political ideologies, as it can be done from a person's home computer and grabs the attention of millons of people over the course of a very short time. No longer are activists confined to demonstrations within their immediate area; now, those with a voice can yell loud enough that the whole world hears them.
References:
Orza:
"Mexican Hackers Declare Electronic War". The Hacktivist. 08 May 1998. 05 December 2008. http://www.thehacktivist.com/archive/news/1998/MexicanHackers-Reuters-1998.pdf
"Crackers: We Stole Nuke Data". WIRED. 06 March 1998. 05 December 2008 http://www.wired.com/news/technology/0,1282,12717,00.html
"Electronic Civil Disobedience and the World Wide Web of Hacktivism". The Hactivist. November 1998. 05 December 2008 http://thehacktivist.com/archive/edt/wwwhack.html
"The Hacker Manifesto". Mithral. 08 January 1986. 05 December 2008 http://www.mithral.com/~beberg/manifesto.html
"Hacker" Wikipedia: The Free Encyclopedia 04 December 2008. 05 December 2008 http://en.wikipedia.org/wiki/Hacker
"Activism" Wikipedia: The Free Encyclopedia 20 November 2008. 05 December 2008 http://en.wikipedia.org/wiki/Activism
"The Golden Age of Hacktivism" WIRED. 22 September 1998. 05 December 2008 http://www.wired.com/politics/law/news/1998/09/15129
Chung, Andrew. "Using a personal computer to hoodwink the censors; REVENGE OF THE NERDS; Three computer geeks at the U of T are renowned developers of anti-censorship software, including a program out this month that could allow people to outwit the world's most repressive regimes". 7 May 2006. Retrieved On 1 December 2008 from Canadian Newsstand Database at http://ezproxy.lib.ucalgary.ca:2048/login?url=http://proquest.umi.com/pqdweb?did=1033073641&sid=1&Fmt=3&clientId=12303&RQT=309&VName=PQD
"Hacktivism". 15 January 2008. Retrieved On 28 November 2008 from http://sniggle.net/hacktivism.php
Meeks, Brock. "India has scary nuke hack". 6 June 1998. 01 December 2008 http://news.zdnet.com/2100-9595_22-99683.html
Nichols, Shaun. "'Hacktivism' making a comeback". 30 April 2008. 05 December 2008 http://www.vnunet.com/vnunet/news/2215510/hacktivism-making-comeback
Myers, Rob. "Hacktivism: The Making of a Hacker Culture". 1 June 2008. 04 December 2008 http://slash.autonomedia.org/node/11110
Doctorow, Cory. "Hacktivism Demystified". 22 April 2002. 03 December 2008 from http://www.boingboing.net/2002/04/22/hacktivism-demystifi.html
Winder, Davey. "US Presidential Campaign Hacktivism: first Palin, now O'Reilly". 21 September 2008. 05 December 2008 http://www.itwire.com/content/view/20741/53/
Howe, Calev. "Hacktivist Gets Into Palin Email". 17 September 2008. 05 December 2008 http://news.aol.com/political-machine/2008/09/17/left-wing-group-hacks-palinss-email/
Marcetic, Zoran. "March". 2003. Retrieved on 05 December 2008 from http://www.diplomacy.edu/Diplo/Calendar2004/
Yi:
"Political hacking: Crime or activism?". Search Security. 13 December 2000. 05 December 2008 http://searchsecurity.techtarget.com/news/article/0,289142,sid14_gci506135,00.html
"ONLINE CRIME". CBS News. 05 December 2008 http://www.cbsnews.com/elements/2007/03/22/in_depth_scitech/frameset2598946.shtml
"Hackers Take Aim". CBS News. 15 July 2002. 05 December 2008 http://www.cbsnews.com/stories/2002/07/12/tech/main515044.shtml
"SOME THOUGHTS ON THE IDEA OF "HACKER CULTURE"". Subsol. 03 June 2002. 05 December 2008 http://subsol.c3.hu/subsol_2/contributors3/riemenstext.html
"Activism, Hacktivism, and Cyberterrorism: The Internet as a Tool for Influencing Foreign Policy". iwar. 05 December 2008 http://www.iwar.org.uk/cyberterror/resources/denning.htm
"Hacking Bhabha" Forbes. 16 November 1998 05. December 2008 http://www.forbes.com/1998/11/16/feat.html
"HOW TO BE AN ACTIVIST". Sierra Club. 05 December 2008 http://www.sierraclub.ca/national/activist.html
"Defending Islam, hacker defaces thousands of Dutch websites" itworld. 28 August 2008. 05 December 2008 http://www.itworld.com/security/54552/defending-islam-hacker-defaces-thousands-dutch-websites
"THIS IS THE JARGON FILE, VERSION 4.3.1, 29 JUN 2001". IWS-The Information Warfare Site. 29 June 2001. 05 December 2008 http://www.iwar.org.uk/hackers/resources/faq/jargon.htm
Paola Di Maio "Internet Europe: Hacktivism, Cyberterrorism Or Online Democracy?". IWS-The Information Warfare Site. 19 March 2001. 05 December 2008 http://www.iwar.org.uk/hackers/resources/hacktivism-europe/internet-europe.htm
Sproule:
"Hacktivism." Wikipedia: The Free Encyclopedia. 19 November 2008. 05 December 2008 http://en.wikipedia.org/wiki/Hacktivism
"What Is Hacktivism?." The Hacktivist. 22 June 2006. 05 December 2008 http://www.thehacktivist.com/?page_id=97
"What is Electronic Civil Disobedience?." The Hacktivist. 22 June 2006. 05 December 2008 http://www.thehacktivist.com/?page_id=98
"Hacktivism and How It Got Here" WIRED. 14 July 2004. 05 December 2008 http://www.wired.com/techbiz/it/news/2004/07/64193
"The Golden Age of Hacktivism" WIRED. 22 September 1998. 05 December 2008 http://www.wired.com/politics/law/news/1998/09/15129
"Hacktivism and Indy Media" Caslon Analytics. November 2004. 05 December 2008 http://www.caslon.com.au/politicsguide4.htm
"hacktivism." Information Security. 05 June 2007. 05 December 2008 http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci552919,00.html
"Sri Lankan virus spreads political message." SOPHOS. 18 May 2001. 05 December 2008 http://www.sophos.com/virusinfo/articles/mawanella.html
Touretsky, David. "Gallery of CSS Descramblers". 13 February 2008. Retrieved On 30 November 2008 from http://www.cs.cmu.edu/~dst/DeCSS/Gallery/index.html
"Hacktivism - ASCII". 27 June 2007. Retrieved On 29 November 2008 from http://scii.nl/hacktivism
"Electronic Civil Disobedience". 12 December 1998. Retrieved On 28 November 2008 from http://web.archive.org/web/19990117034226/http://www.nyu.edu/projects/wray/ecd.html
Clark:
"Blogs about: Hacktivist." WordPress.com. 28 August 2008. 05 December 2008 http://wordpress.com/tag/hacktivist/
"Cult of the Dead Cow." Wikipedia: The Free Encyclopedia. 29 September 2008. 05 December 2008 http://en.wikipedia.org/wiki/CULT_OF_THE_DEAD_COW
"Denial-of-service attack." Wikipedia: The Free Encyclopedia. 4 December 2008. 05 December 2008 http://en.wikipedia.org/wiki/Denial-of-service_attack
"Oxblood Ruffin." Wikipedia: The Free Encyclopedia. 20 October 2008. 05 December 2008 http://en.wikipedia.org/wiki/Oxblood_Ruffin
"Meet the 'Hactivist'." COMPUTERWORLD. 16 October 2000. 05 December 2008 http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=52405
"Inside the world of a 'hactivist'." CNN.com. 18 October 2000. 05 December 2008 http://archives.cnn.com/2000/TECH/computing/10/18/hactivism.idg/index.html
“Cultural Activism On the Internet”. //William Thake's Web Design Portfolio . 05 December 2008 http://www.english.ilstu.edu/bmthake/folio/docs/culturalactivism.html
“Online Civil Rights After September 11th - The threat to the right to protest online from the war against terrorism ”. IWS-The Information Warfare Site. . 05 December 2008 http://www.iwar.org.uk/hackers/resources/electrohippies-collective/op4.pdf
Carrie Kirby “Hacking With a Conscience Is a New Trend”. SFGate. 20 Novemver 2000. 05 December 2008 http://www.sfgate.com/cgi-bin/article.cgi?file=/chronicle/archive/2000/11/20/BU121645.DTL
Naomi Klein “Computer Hacking New Tool of Political Activism” The Toronto Star . July 23, 1998. 05 December 2008 http://www.gis.net/~cht/torontostar.html