Click Here to See What You Have Won

To See What You Have WON!!!
Contents
- 1 Group name
- 2 Group Members
- 3 Initial Problem Statement
- 4 Argument
- 5 Introduction
- 6 Why do people click on pop-ups?
- 7 What Scams Look Like
- 8 What Happens When You Click Here
- 9 How Scammers Use Stolen Infromation
- 10 How to Avoid Being Scammed
- 11 Legislation to Protect Users from Scams
- 12 Conclusion
- 13 References
- 14 Phishing Scam Legislation
Group name
Group Members
Katie Boone, Agata Walny, Junice D'Silva, Shou-Chih Hsu
Initial Problem Statement
To address the general problem of pop ups, and how they scam personal and financial information
- How they "pop-up" - Why they are so attractive - What scams look like - How they scam money from people who "Click Here" - How to avoid being scammed - How the problem can be solved.
Argument
Popups were originally designed to help in the display of information but have become a serious threat. They are an annoyance to computer-users around the world. But not only that, various scams have been created that take money from unsuspecting users. The risk has become so great that judicial action has been taken to combat these hidden crimes. Our project will address these and other issues regarding pop ups as well as how to block them.
Introduction
It is hard to believe that pop up windows were originally a useful application. They were first designed to display information that was separate from the main webpage. This way, two different sources can be seen without any interference with the current browser. There are two general types of pop ups, normal pop ups and alarm pop ups. Normal pop ups display information that has been requested, such as music/video downloads or email. They are also used to display advertising marketed specifically to consumers visiting the website. Alarm pop-ups indicate a problem with your computer system. These pop ups occur in a “browser flood” as soon as a browser is opened. This indicates that spyware is running on the system and that these pop ups are no longer trying to help, but trying to hurt you. Pop ups are generally encoded by Javascript in the computer language of the website or browser. This language will indicate how the pop up appears on the screen. This can be in a “Pop Over”, “Pop Under” or “Timed Pop up” fashion.
Why do people click on pop-ups?
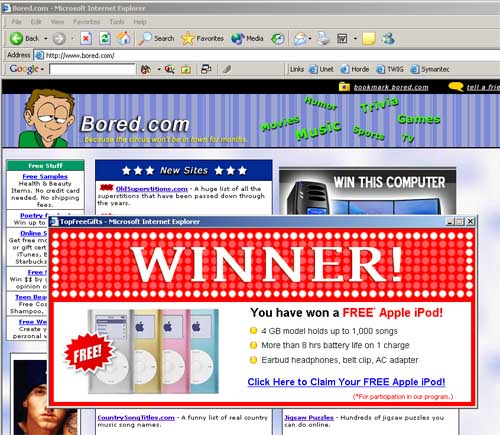
So why do people click on pop-ups? It is the same reason why people buy certain products over others. Advertising and appearance plays a huge role in taunting and persuading people to click on that little flashing box. When a pop-up appears on your screen, most people will just close it by pressing the little “x” in the corner. How do people who create these pop-ups stop you from doing this? Some pop-ups have a fake ‘close’ button that when pressed, instead of closing the pop-up will open another page and perhaps a few more pop-ups. Some pop-ups will also tease you with games and false promises. Here is an example of such a pop up which contains both a game and a false promise. It is known as "hit the monkey" and often appears when the internet browser goes to "Myspace.com".





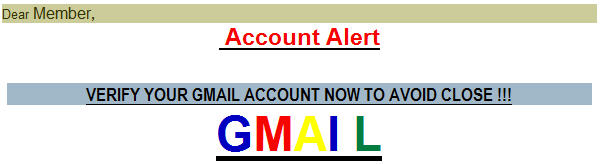
What Scams Look Like
The main type of scam used by pop ups is called a phishing scam. These scams tell you to “Click Here” for a prize, money or just for fun and re-direct you to a different site. These pop ups make the internet user vulnerable because they play on the trust of the user. If the user opens a credible and trusted website as well as a malicious website the malicious website can display information in a pop up window which will appear to be from the credible site. The user trusts this pop up because it appears to be from a trustworthy site even though it is not.
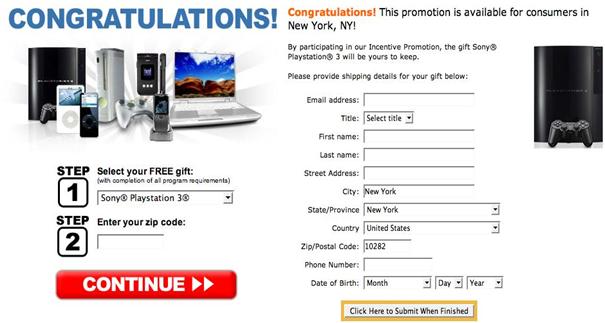
What Happens When You Click Here
After the apparently trustworthy pop up has been clicked it redirects the browser to a different malicious site. This site is generally a cheap replica of a credible website to, again, play on the trust of the user. The site will congratulate the user for winning the prize and will ask for personal and financial information. For most people this would be a time to stop and think about who will be receiving the information but surprisingly many people do fall victim to this scam. The fact that the site seems credible is a large determinant of whether or not the user will enter their information. Once the information has been entered the site will promise a prize in 3-6 weeks. It is not until this time that the user realizes they have been scammed.

How Scammers Use Stolen Infromation
If an email account password or user name is stolen scammers can send out phishing e-mails to the victim's friends using the victim's account. This way the scammer can steal infromation from both the victim's email account and the victim's friends. If the scammer steals information such as a bank account number, credit card number or username and password, scammers will gain full access to the victim's personal and financial information. With this power the scammer can transfer funds to other accounts, issue cheques in the victim's name, conduct the victim's transactions, etc. The scammers may even change the victim's account passwords, so the victim can no longer access their account. The identity of the victim may potentially be stolen in this fashion. If such an extreme circumstance occurs the scammer is essentially "above the law" in that they can now commit fraudulent and criminal activities while using the victim's name.
How to Avoid Being Scammed
The easiest way to avoid being scammed is to be smart when using the internet. Don’t rely only on the apparent credilbility of the site, question who will be getting your information and why they are asking for it. Certainly, if you have a bad feeling about the site DON’T ENTER YOUR INFORMATION!!! Most important of all, no matter how great that free trip to tahiti sounds DO NOT CLICK ON QUESTIONABLE POP UPS. Scams aren't the only use for pop ups, they are dangerouse because they can be linked to any site, any virus and any sketchy person on the web. In saying this it is also important to note that not all pop ups are out there to hurt you and your computer. The key is to be weary of questionable sources and offers. As was said in the introduction, pop ups can be used in useful ways. They can be used to sign in to a main site, display additional information or can redirect you to an email site. The fact of the matter is that you can never be too cautious when dealing with the internet and your personal information.
Legislation to Protect Users from Scams
The anti-phishing act of 2005
This law criminalizes the action sending a phishing email or creating a phishing pop up or website regardless of whether any unsuspecting users suffered any actual damage. This act will decrease the amount of phishing websites, pop ups and emails because it criminalizes not only actively scamming people but the attempt to scam people. There is no proof of damage needed, just evidence of an attempt to achieve personal or financial information without just cause.
Internet legislation can be tricky in that it is very hard to catch people in the act and actually identify who they are. Although this act does broaden the category of internet crime (attempt instead of action), laws such as this will only be effective once there is a clear cut way of identifying who people are on the web. There are many other issues involved here; one of the largest is one’s first amendment rights. If the government is able to identify phishers will it be able to identify everyone? As you can see this is a tough situation. The most important information to take away from this is that legislation seems like an easy fix but it isn’t always as easy as it seems. This type of legislation is more of a comfort blanket than an actual solution because people will feel protected even though there is no solid way of finding criminals. It is more important to rely on your own knowledge and not get drawn into internet scams than to rely upon seemingly flawless legislation.
Conclusion
There are many ways that you can stop popups from attacking your computer. Since many pages use Javascript for display purposes, turning off Javascript will give you a great advantage over the amount of popups that appear on your screen. Many software programs disable popups from opening up. Nowadays this is usually installed with your web browser. (Mozilla and Internet Explorer 7 include codes that disable popups from appearing during your internet experience) Most browser bars now include a popup blocker, so installing one will stop most if not all of them from popping up. (Google bar is a very good one)
Since there are many ways that pop-ups will appear on your screen (pop over, under and timed), it is best to install a popup blocker on your browser to stop any of them from opening up.
If all else fails, and you still keep getting pop-ups the best thing to do is not click on them!
Try your hand at "Kill the Popups": http://www2.b3ta.com/realistic-internet-simulator/
References
How "pop-ups" infect a computer.
http://pcworld.about.com/news/Dec092004id118878.htm
http://www.acewigs.com/shop/wigs/News/13704.php
http://technology.timesonline.co.uk/tol/news/tech_and_web/article1464355.ece
http://www.albany.edu/its/damage_control_computer_infections.htm
http://www.news.com/Pop-up-program-reads-keystrokes%2C-steals-passwords/2100-7349_3-5251981.html
http://www.practicepro.ca/LawPROmag/TechTipDisarmingPopups.pdf
http://www.free-web-browsers.com/your-computer-is-infected.shtml
http://www.yourtechonline.com/art24_spydawn.php
http://www.pcworld.com/article/id,119016-page,1/article.html
http://www.cbc.ca/news/background/computer-security/safe_practices.html
http://www.pc-care.ca/services/spyware.html
http://forums.spywareinfo.com/index.php?showtopic=57307&pid=298478&mode=threaded&start=
http://forums.whatthetech.com/smitfraud_c_msvps_with_security_warning_pop_ups_t84780.html
How to get rid of Popups
http://www.pcanswer.com/articles/synd_spyware2003.htm
http://filext.com/faq/get_rid_of_popups.php
http://www.masternewmedia.org/news/2004/01/30/get_rid_of_popups_and.htm
http://www.howtogetridofstuff.com/computer-problems/how-to-get-rid-of-pop-ups
http://www.getridofthings.com/get-rid-of-popups.htm
http://ezinearticles.com/?5-Simple-Effective-Ways-to-Get-Rid-of-Popups-on-Your-Computer&id=587682
http://www.youtube.com/watch?v=CwGx9sokorE (online tutorial on how to get rid of popups on firefox)
http://www.itcompany.com/popup.htm
http://www.videojug.com/film/how-to-stop-pop-ups (another online tutorial video)
http://windowsxp.mvps.org/Popups.htm
How they scam money from people who "Click Here"
http://www.about-the-web.com/shtml/scams.shtml
http://www.hoax-slayer.com/internet-scams.html
http://en.wikipedia.org/wiki/Internet_fraud
http://www.fraud.org/tips/internet/general.htm
http://www.livedatesearch.com/internet_dating_scam.html
http://www.sec.gov/investor/pubs/cyberfraud.htm
http://www.usdoj.gov/criminal/fraud/internet/
http://en.wikipedia.org/wiki/Advance_fee_fraud
How Pop Ups Work
http://www.openjs.com/tutorials/advanced_tutorial/popup.php
http://www.freedownloadscenter.com/Best/how-popups-work_R2.html
http://javascript.internet.com/generators/popup-window.html
http://www.w3schools.com/js/js_popup.asp
http://blogs.techrepublic.com.com/security/?p=401
http://www.astro.rug.nl/~gipsy/pguide/gui-example9a.html
http://developer.mozilla.org/en/docs/XUL:PopupGuide
http://webdesign.about.com/od/advertising/i/aa021703a.htm
http://www.theregister.co.uk/2003/11/06/ftc_gets_injunction_against_popup/
http://www.dcourier.com/main.asp?SectionID=1&subsectionID=1&articleID=52274
http://articles.techrepublic.com.com/5100-1009_11-5818568.html
http://www.whoswatchingcharlottesville.org/phishing.html
Phishing Scam Legislation
http://www.phishingdangers.com/
http://www.law.duke.edu/journals/dltr/articles/2005dltr0006.html
