T11 Group 5
Unauthorized Access
Contents
Group Information:
CPSC 203 Fall 2008 -- Section L02 -- Tam
CPSC 203 Fall 2008 -- Turorial 11 -- Tanvire elahi
Group 5: Yuan Yuan, Kim Soyeon
(source of this picture: Chinadaily, Nov 14 2008, http://www.chinadaily.com.cn/world/2006-03/20/content_547328.htm)
Project Statement:
Research Methodology
We select the topic "Unauthorized Access", and will focus on both technical sides and legal side. We will learn what is unauthorized access and what is its effect. For better understanding, the case study will be present in the research. After knowing it better, we may focus on the prevention of this action.
Goal
Unauthorized access is becoming a big issue as the increased use of broadband Internet access (cable or ADSL) where computers are always connected. The goal for this project is to understand an unauthorized access to reduce its threats.
Introduction:
Professional Definition
1. "Unauthorized Access is when a person who does not have permission to connect to or use a system gains entry in a manner unintended by the system owner." (University of Tennessee,Nov 9 2008, https://my.tennessee.edu/portal/page?_pageid=40,614533&_dad=portal&_schema=PORTAL)
2. "Unauthorized Access is gaining access into any computer, network, storage medium, system, program, file, user area, or other private repository, without the express permission of the owner. Unauthorized access is the same as theft." (State of Michigan, Nov 9 2008, http://www.michigan.gov/cybersecurity/0,1607,7-217-34415---,00.html)
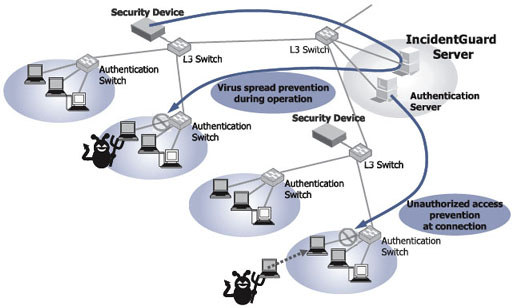
(source of this picture:NEC Coporation, Nov 14, http://www.nec.co.jp/techrep/en/journal/g06/n01/060105-3.html)
Statistics:
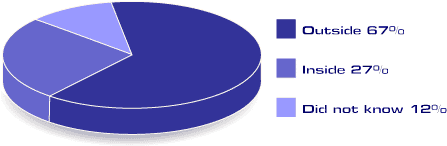
According to the 2002 Computer Security Institute (CSI) / Federal Bureau of Investigation (FBI) Computer Crime and Security Survey, large number of people have experienced the unauthorized access. Because Canadian statistics are usually very similar to those in the USA, this statistics can be used to see the trend of computer security in Canada. The survey are as follows:
(Source: 2002 CSI/FBI Computer Crime and Security Survey, http://www.cse-cst.gc.ca/tutorials/english/section1/m1/s1_1_10.htm)
The 2002 statistics show that 67% have experienced unauthorized computer use within the last twelve months; 27% say they have not; and, 12% did not know.
Effect:
The main effect of unauthorized access is loss of private information, which is a severe problem. For instance, the person who got your bank account number and password can access to your account and take away all your money in that account. The criminal can slao use your identity to do some illegal things, and bring you a lot of trouble. For better understanding, let's look at the case study following.
Case:
Case 1: Unauthorized Access at North Bay
"Jessica Quitugua Sabatia, a former accounts payable clerk for North Bay Health Care Group, admitted to using her computer to access North Bay’s accounting software without authorization, and in turn issued approximately 127 checks payable to herself and others. Several of the checks were cashed by Sabatia or deposited into her personal bank account, and some were deposited into the bank accounts of others. She attempted to conceal the fraud by altering the electronic check registers of North Bay to make it appear as if the checks had been payable to the company’s vendors. The fraudulent scheme resulted in losses to North Bay of at least $875,035."
"On May 27, 2004, Sabatia, plead guilty to two counts of computer fraud, and faces a maximum sentence of five years in prison and a $250,000 fine." (Wikipedia,Nov 11 2008, http://en.wikipedia.org/wiki/Computer_fraud_case_studies#Case_1:_Unauthorized_Access_at_North_Bay)
Case 2:Experts to fight online "phishing' schemes
"Washington - The e-mails look real. A bank needs to "verify" your account information. An online payment service urgently warns about "unauthorized" access to your account."
Many criminals use this method to access your account. According to the statistics summarized by some experts, "last year found 43 percent of US adults had received at least one of the bogus e-mails. Of those, about one in 20 -- or 4.5 million people -- provided the requested information, and about half of those end up being victims of theft or identity fraud.Many US victims end up handing over their social security numbers or other personal information that can be used to open bank or credit accounts or other types of fake identity. "
""Victims report an average loss of 600 dollars, but if their social security number is compromised, the damage is much more profound," said Susan Grant, head of the National Consumers League's fraud information center and a participant in a recent summit of technology firms, financial institutions and others aimed curbing phishing. "
With the increasing in this type of crime, exports began to take action.They used the method "authentication," which helps the user to recognize wheather an email is real. However, it is not a easy job because this technology is hard to get executed. As
Peter Swire , an Ohio State University law professor involved in the anti-phishing gathering, indicating, "It has to be secure by design, so grandma doesn't have to be a computer expert."
"A report by security firm Symantec found that during the last half of 2005, 7.92 million daily phishing attempts were identified, an increase over the 5.70 million attempts per day in the previous six months. Symantec expects even more growth in this type of scam. "Based on the report, Arthur Wong, vice president of Symantec Security Response once said "This and other forms of cybercrime "represents today's greatest threat to consumers' digital lifestyle and to online businesses in general."
According to the experts' report, the traditional target of the criminals is the big organization such as banks, but now they have begun to target small groups.
"A Consumer Reports survey conducted in late 2005 found nine out of 10 US Internet users over 18 have made changes to their online behavior due to fear of identity theft -- with 30 percent cutting back their overall use of the Web. Another survey by eMarketer estimates that over a third of US Internet users do not buy online, mainly due to concerns over the security and privacy of personal information. "
Due to the wide use of internet, Phishing becomes a blobal issue which has the major effect - unauthorized access. Experts in United States stated "Many of the attacks originate from outside the United States, so we need cooperation from our international partners."
(Chinadaily, Nov 14 2008, http://www.chinadaily.com.cn/world/2006-03/20/content_547328.htm)
Protection:
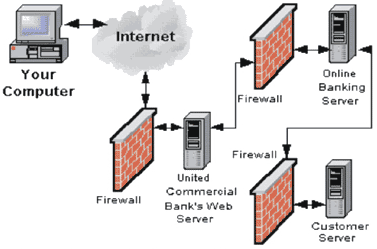 (source of the picture: United Commercial Bank, Nov 14 2008, http://www.ibankunited.com/ucb/security.html)
(source of the picture: United Commercial Bank, Nov 14 2008, http://www.ibankunited.com/ucb/security.html)
Who is responsible?
Security is the responsibility of everyone who uses and benefits from the system.
This includes:
* Senior Management * IT Security Management * Program and functional managers/application owners * Technology providers * Supporting organizations and/or functions * Users
Even safeguards exist for security, it is your responsibility to ensure that it is working.
(More details in (http://www.cse-cst.gc.ca/tutorials/english/section1/m1/s1_1_6.htm)
How to protect?
Detect The Unauthorized Access
1)By using Windows Security Log
2)By using IIS (Internet Information Systems) logs
(More details in (Microsoft Corporation,Nov 13 2008, http://fentyler.co.uk/iisHelp/iis/htm/core/iidetsc.htm))
Anti-spyware Software
Spyware is a software that performs certain behaviors such as advertising, collecting personal information, or changing the configuration of your computer, generally without appropriately obtaining your consent first.
Commonly spyware get into your computer by installing the software during the installation of other software you want such as a music or video file sharing program. Spyware can be installed simply by clicking to an image of an adult site.
To prevent this situation, we can use the Anti-spyware software such as Windows Defender to check whether the spyware entered your computer as well as to clear the existing spyware in your computer.This kind of software can help us a lot, but we still have to be aware of that there is no perfect software. Thus we also need to be careful about opening a suspicious website, or a suspicious email.
(More details in (Information-technology Promotion Agency, Nov 14 2008, http://www.ipa.go.jp/security/english/virus/press/200601/E_PR200601.html),http://www.microsoft.com/protect/computer/basics/spyware.mspx,http://www.microsoft.com/protect/computer/spyware/prevent.mspx))
Encryption
As we learned in this lecture, the encryption technology helps to protect our information by encoding the transmitted data using a mathematical formula which scrables the information. Without a corresponding decoder, the transmission would look like garbled text. (Citicorp, Nov 14 2008, http://www.citibank.com/singapore/ipb/english/ibank/security/)
Firewalls
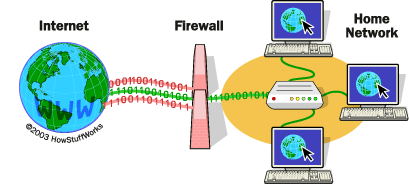 (Source: http://www.howstuffworks.com/firewall.htm)
(Source: http://www.howstuffworks.com/firewall.htm)
As we learned in the course CPSC 203, firewalls are system which can help to prevent the unauthorized access. It is a barrier to keep destructive forces away from your property. Firewalls implement security rules such as allowing access of servers to certain computers. Firewalls can be implemented in both hardware and software, or a combination of both.
The firewall that exists today takes many forms such as Screening routers, application gateways and authenticagting servers which are explained below.
(More details in (Syntek Computer Group, Nov 17 2008, http://www.syntek.net/chinese/technology/Internet%20Security%20Primer.htm), (http://computer.howstuffworks.com/firewall.htm), http://www.webopedia.com/TERM/f/firewall.html))
Proxy Servers
The proxy server is used to access Web pages by the other computers. When another computer requests a Web page, it is retrieved by the proxy server and then sent to the requesting computer. The net effect of this action is that the remote computer hosting the Web page never comes into direct contact with anything on your home network, other than the proxy server.
(More details in (http://computer.howstuffworks.com/firewall4.htm))
Screening Routers
Packets (small chunks of data) are analyzed against a set of filters. packets that make it through the filters are sent to the requesting system and all others are discarded. It reduces the amount of user to access or connect, and totally refuses the unauthorized or unknown users to enter or access.
(More details in (Syntek Computer Group, Nov 17 2008, http://www.syntek.net/chinese/technology/Internet%20Security%20Primer.htm),(http://computer.howstuffworks.com/firewall1.htm))
Stateful Inspection
It doesn't examine the contents of each packet but instead compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
(Source: http://computer.howstuffworks.com/firewall1.htm)
Legality of Unauthorized Access:
In Canadian law, unauthorized access is addressed by Section 342.1 of the Criminal Code of Canada. According to Section 342.1, "Every one who, fraudulently and without colour of right" obtains "computer services" from an access point is subject to criminal charges. (Criminal Code of Canada, http://www.canlii.org/ca/sta/c-46/sec342.1.html)
Conlusion:
With an understanding of unauthorized access, people need to be aware of unathorized access to reduce today's threats and tomorrow's potential threats.
Links:
1. https://my.tennessee.edu/portal/page?_pageid=40,614533&_dad=portal&_schema=PORTAL
2. http://www.michigan.gov/cybersecurity/0,1607,7-217-34415---,00.html
3. http://www.computerhope.com/issues/ch000464.htm
4. http://www.npa.go.jp/cyber/english/legislation/ucalaw.html
5. http://fentyler.co.uk/iisHelp/iis/htm/core/iidetsc.htm
6. http://www.ipa.go.jp/security/english/virus/press/200601/E_PR200601.html
7. http://www.ipa.go.jp/security/english/virus/press/200601/ua200601-e.html
8. http://www.dba-oracle.com/t_unauthorized_access_computer_network_crime.htm
9. http://www.chinadaily.com.cn/world/2006-03/20/content_547328.htm
10. http://www.syntek.net/chinese/technology/Internet%20Security%20Primer.htm
11. http://www.russharvey.bc.ca/resources/security.html
12. http://www.cse-cst.gc.ca/tutorials/english/section1/m1/s1_1_10.htm
13. http://www.cse-cst.gc.ca/tutorials/english/section1/m1/s1_1_6.htm
14. http://en.wikipedia.org/wiki/Legality_of_Piggybacking
15. http://www.canlii.org/ca/sta/c-46/sec342.1.html
16. http://www.howstuffworks.com/firewall.htm
17. http://computer.howstuffworks.com/firewall1.htm
18. http://computer.howstuffworks.com/firewall4.htm
19. http://www.webopedia.com/TERM/f/firewall.html
20. http://www.microsoft.com/protect/computer/basics/spyware.mspx
21. http://www.microsoft.com/protect/computer/spyware/prevent.mspx