THE IT COPS : Identity Theft
Identity theft is defined as the deliberate and wrongful act of obtaining someone's personal information typically for economic gain, though there can be other motives, such as evasion of law. In 2006, almost 8000 victims reported losses of (CDN) $16 million in identity theft[1] to PhoneBusters, the Ontario Provincial Police, Royal Canadian Mounted Police (RCMP) and Competition Bureau Canada-managed anti-fraud call centre in Canada. The Canadian Council of Better Business Bureaus has estimated that identity theft may cost Canadian consumers, banks and credit card firms, stores and other businesses more than $2 billion annually.[2] From January 1 to December 31, 2008, 11,370 complaints by Canadian victims were made to PhoneBusters, and the money lost from that in total was (CDN) $9,590,385.05.[3]
Contents
Who We Are
Due to the wide usage and growing accessibility of information on the internet, the World Wide Web has become more and more of a minefield for those not acquainted with the ever-growing methods of identity theft. Our group is dedicated to the mission of spreading the word of such theft as pertaining to computers, and thus hope to arm the general public with prevention know-how. We are... the IT COPS!
IT Cops, T27 Division
- Arun Brar
- Chris Chung
- Wei Dai
- Tenzin Dratsangshema
- Kevin Feng
Phishing
Definition
Webopedia defines phishing as: “The act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. The Web site, however, is bogus and set up only to steal the user’s information.” Phishers may disguise themselves as just about any company/institution, from financial ones (i.e. banks) to even government agencies. Other terms for phishing include email/website “spoofing,” or “carding.”
The term for phishing derives from the word “fishing,” to convey the sense that this act intends to cast “bait” (the bogus e-mails) in the hope that someone will bite (i.e. be tricked into giving away their personal information). The “ph-” substitution of the “f-” in phishing goes back to hackers’ frequent substitution of “f” with “ph.”
The original form of phishing entails spreading spam messages to untold millions of mailboxes, in the hope that even a few fall for the trap. Here, then, is the analogy with fishing: most of the "fishes" (the target audience) will not take the "bait" (the seeming authenticity of the phishing e-mail), but of the countless number of them in the "ocean" (the internet), a few will, and that is often all that is really needed to ensure the gain of the "fisher" (phisher).
How to detect- Characteristics:
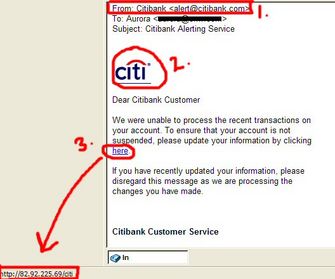
1) The main characteristic of phishing e-mail messages is that they ask for personal data, or direct you to Web sites or phone numbers to call where they ask you to provide personal data.
2) The “From” address appears to be legitimate, although it is often very easy to make it so without actually being part of the original company. Includes images and logos that can easily be taken from the Internet.
3) Often gives you a premise/incentive for taking serious note of the e-mail and following their instructions. Common phrases centre around things like:[4]
- "Verify your account." Businesses should not ask you to send passwords, login names, Social Security Numbers, or other personal information through e-mail.
- "You have won the lottery." Phishing e-mails often designate you as a winner of a contest of some kind without any prior application, and asks for your personal information to claim your prize. Try to remember if you have applied for a lottery or some type of contest/draw from the company before. If you have not, there’s obviously something "phishy" about it (Cue lame laughter). If it’s too good to be true, it often is.
- "If you do not respond within 48 hours, your account will be closed." This conveys a sense of urgency and may prompt recipients to act without thinking. May include phrases like, “Your account has been compromised. Please respond to reactivate it.”
4) Usually includes a clickable link that directs you to an official-looking website, where they hope you will give your personal information away. The hyperlink’s appearance is often falsely and deliberately typed to display a legitimate and official-looking URL (weblink). This can be done through HTML, so that what the hyperlink displays does not correspond to the actual URL. For example, in one case, the weblink displayed showed “https://oIb.westpac.com.au/ib/defauIt.asp.” After hovering the mouse over the link, at the bottom left corner of the screen, the real link was found to be “http://olb.westpac.com.au.userdll.com:4903/ib/index.htm.” In HTML, the code could be something like: <a href= http://olb.westpac.com.au.userdll.com:4903/ib/index.htm> https://oIb.westpac.com.au/ib/defauIt.asp</a>.
5) The bogus website looks real, frequently giving you something like a login page, which obviously asks for your personal information. It collects your login information when you type it in.
6) The occurrence of spelling and grammar mistakes, some characters seemingly accidentally replaced with others (for example, the use of lower case L’s for replacing lowercase I’s), and the addition of hidden words (i.e. written in white to appear invisible due to the standard white background of an e-mail), which are deliberately done to avoid standard anti-spam detection. Official company messages almost always do not includes such mistakes.
Prevention
1) Never give out personal information through the Internet (i.e. e-mail); it is not secure! From this rule, it should be plain obvious that any e-mail that asks for your personal information is often not authentic. Businesses (or at least well-established ones) never ask for personal information, like your Social Insurance Number and account information.
2) Never click on the links provided by any such e-mails. Doing so may release spyware onto your computer. Delete it, and also delete it from your trash bin, for safeguarding against any accidental clicking.
3) If you really think that the e-mail you received is authentic, contact (i.e. call or e-mail) the company in question to inquire about the message. If you wish, type the URL of the displayed link in the e-mail, as opposed to the quick route of clicking the link, which may redirect you to a fake and dangerous website (as explained previously). However, even this may not be entirely recommended (Let’s just say phishers can be pretty smart). Stick with contacting the company first.
Sharpening the phishing pole: spear phishing
Definition
As discussed earlier, the original method of phishing entailed spreading mass e-mails to as many people as possible, in the hopes that a handful of them would succumb to the trap (even 1% is desirable). However, a new form of phishing has recently taken form: spear phishing. Spear phishing, unlike the original phishing, targets a substantially smaller population, like a single person/member of a company (i.e. an employee), a department of a company, etc. In this, the phisher disguises himself as coming from a position of high authority, such as a boss, a higher-ranking level of administration, human resources, staff from the IT (information technologies) department, etc., and often asks things like updating personal information. In the face of such seeming authenticity, authority, and trustworthiness, the victim often follows the instructions to his/her great peril.
Prevention
As with the original brand of phishing, be aware and cautious. Never, ever give personal information through e-mail. It is not secure! Verify that this message is real by calling your head or the sender of the e-mail (i.e. the human resources department).
Chat Rooms
What are chat rooms?
Chat rooms are meeting places on the Internet where the user can start or join live, real-time conversations with people across the world. There are three forms of online chat, Web-based, Real-time, and Internet Relay Chat (IRC). Web-based chat rooms are forums which may be devoted to particular topics (e.g. movies, sports, music etc.) that allow for messages to be written and read in real time by all individuals who are present in the room at the time. Real-time chat often called IM’s (Instant Messaging), allow for individuals to converse with one another in real time but only if they have been added to a “friends” list. Finally, Internet Relay Chat or IRC involves individuals who communicate with users around the world in real time and who are connected to the same network or server. Similar to the web-based chat rooms, IRC conversations are theme based as well.
Furthermore, chat rooms can be either public or private conversations. Public chat rooms enable users to communicate with each other in a public online setting. A private chat room setting occurs when the user initiates or accepts private messages or one-on-one chat sessions. Some chat room conversations can be controlled by monitors who manage what is written before it is viewed by others and have the ability to remove a participants from the room if they act inappropriately. Chat room conversations may also be led by a moderator who overseas a particular topic or discussion with the users and others may be unmonitored open conversations in chat rooms.
Risks
Since it is difficult to control all the information available on the Internet, there are a variety of risks that are associated with chat room use alone. These threats may involve, online bullying or harassment, internet luring, and fraud. Eventually these threats can result in the physical harm, non-physical harm (i.e. loss of money, mental well being, stress, etc.) or possibly both, to individuals within society.
In particular, our focus will be on Identity Theft in chat rooms as it is a growing concern and is actually a place where identity theft can occur. Online predators constantly search for people they can befriend and gain their trust in order to collect personal information and possibly money from them. These so called “friends” may also send links containing Trojan horses or Viruses which infect the computer system and allow for hacking and stealing of personal information. Social networking sites, such as Facebook and MySpace are fast becoming a target of information that thieves can use to gather photos and more personal information on the individuals they chat with.
They might assume the stolen identity of another person, or identity impersonation, in order to gain the trust of the individual(s) that they are chatting with. In an article by CNW Group/NEWSTALK 1010 CFRB , two Canadian radio personalities discovered that they were victims of Identity Theft when a Toronto man had called onto the show confessing on air of impersonating them on internet chat rooms. He had even sent personal family photos of both radio personalities to convince others that they were in fact chatting with the actual hosts. In addition, this predator, in the guise of one of the hosts had a three year on-line relationship with various people around the world. This scam had surfaced when the women he had communicated with began emailing the personalities at work asking why their messages were not being responded. The man’s identity was later provided to the police and he did deny meeting with any of the individuals whom he had corresponded with online and using the host's identities to acquire money or favors from people or businesses. However, this does not denote the fact that these individuals whom he had been chatting with had left themselves susceptible to various risks of having personal information taken, loss of money, and harm come to them.
Recently it has become an issue that chat rooms have now become the online black market for hackers selling personal information to predators. There are actually chat rooms where online thieves bond and compare notes, exchange credit card or social insurance numbers, and other valuable information. These cyber criminals post a few identities in the chat room and those that they refer to as fulls "contains enough information to take a thief on a multiyear identity theft ride, as it will include someone’s Social Security number, home phone number, e-mail account and password, debit card PINs, credit-card numbers, and mother’s maiden name. Hackers sell them in bulk for $1 to $5 a pop in an international ring that’s as sophisticated as it is blatant. The chat rooms offer the opportunity to check the validity of stolen credit card numbers in real time.” ID Theft Protect These criminals are smart and they sometimes impart or sell information for cheap by selling used cards to others in order to prevent tracking by investigators.
In addition, these chat rooms often have administrators that have the capability to remove people from a room, set passwords and load programs which allow other hackers to confirm in real time the validity of the stolen credit cards.
Who does this affect?
Both children and adults alike can be affected by this. Cyber criminals seek and prey on users who are vulnerable or naive, in other words, anything that would make it easier for them to steal information quickly.
Children are susceptible to being lured into providing their personal contact information. Predators often conduct online scams where a child is tricked into providing a credit card number or exposing family information.
Adults too can meet with unexpected consequences of unsafe internet chatting. Users can be lured in to friendships that would eventually result in the individual sending money or providing personal information to these thieves. Adults who are looking for companionship can be found on internet dating sites, seniors, users who are not familiar with the internet are just some examples of persons of target for these online criminals.
Prevention
Take your precautions, there are numerous ways that you can protect yourself and your family when chatting online.
Parents and Children:
1) Talk to your children and about their internet usage and risks associated with it and create a handy list of internet rules for the family (i.e. time limits on the computer, not to open attachements that they are unsure of, not to provide contact information or personal information etc).
2) Keep the computer in a common area of your home.
3) Parents can install software which can block certain inappropriate sites for children or can log and provide a detailed account of the websites their child visited, the visited chat rooms and what was said during the conversations.
4) Children between the ages of 10-13 should be in monitored chat rooms and under close supervision of an adult. For teens, it is recommended that they should always be in a monitored chat room and always under the "Public" chat rooms.
5) Parents should also review with their children all names that are on their "friends" list to ensure that they are chatting with friends they actually know.
6) Be informed. Parents should educate themselves about computers and the Internet. In addition, there is certain lingo which is involved with chatting. Chatting Lingo
Adults:
1) Keep personal information (i.e. name, age, date of birth, phone number etc) off of websites and social networking sites.
2) Never divulge personal or financial information to others.
3) Use a "handle" or "nicknames" that are non-identifiable for gender or age.
4) Be cautious when downloading attachments that may be sent.
5) Block senders or leave conversations that make you feel uncomfortable.
6) Take caution when posting photos and post photos that represent you (i.e. clean, safe photos).
7) Do not chat with people you do not know on webcam.
8) Do not arrange to meet in person without taking proper safety measures first. If you feel you should meet, then arrange to meet but with a group of your friends.
9) Save copies of your chat room conversations.
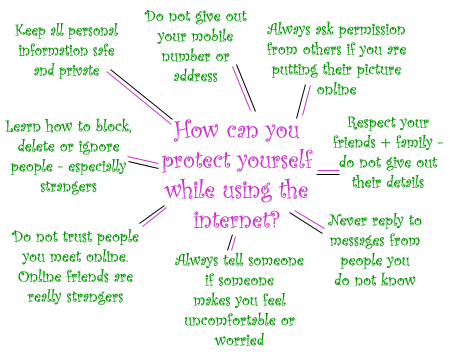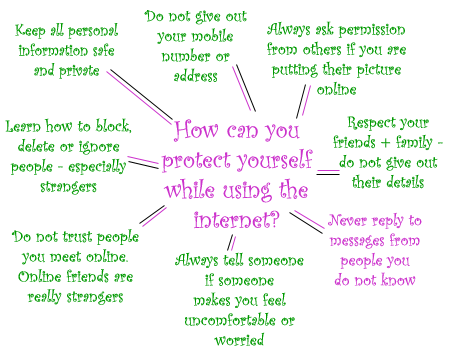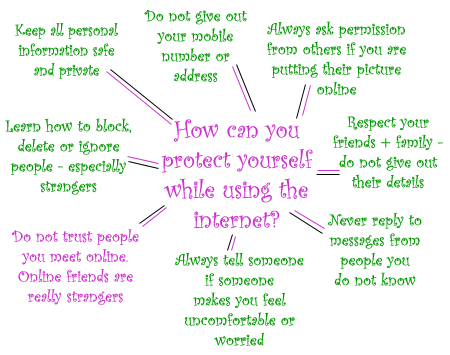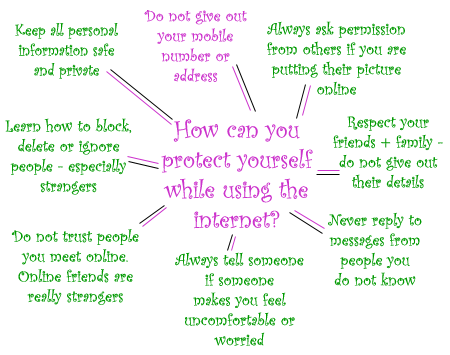
Some additional tips - Protect Yourself Diagram:
Here is a link for a short video on "Internet Safety - Chat rooms" by the Calgary Police Service: Chat Room Safety
RSA
In cryptography, RSA is a mathematician method for public-key cryptography. It is the first algorithm known to be useful for signing as well as encryption, and one of the first significant advances in public key cryptography. RSA is widely used in electronic commerce protocols, and is believed to be secure given long keys and the use of up-to-date technology. When dealing with identity theft, RSA is the first well know method.
History
Ron Rivest [5], Adi Shamir [6], and Leonard Adleman [7] at MIT. RSA is a collection of first letter in each of their last name.
In 1973,a English mathematician named Clifford [8]. Cocks also provides a equivalent method, but his work has considered as national secrecy and not published until 1997.
The RSA is secure because finding roots modulo n is hard. Until 2008, there is no efficient way to decrepit RSA, and technically, if the n is large enough, the decryption of RSA is impossible.
Produce of public and private key
If Alice wants to send a private message to Bob. She can use the following method to produce a public and private key.
- randomly pick two prime [9]pandq,p does not equal to q,calculate N=pq。
- According toEuler's totient function,a number which is smaller than N and shares no common factor than 1 is the number(p-1)(q-1)
- Pick a interger e which share no common factor with the product of(p-1)(q-1), and e is smaller than(p-1)(q-1)
- Use the following the method to calculate d:d× e ≡ 1 (mod (p-1)(q-1))
- Now, erases p and q from the record.
e is the public key,d is the private key. d is secret to the public,andN is known to the public. Alice will send the her public key to Bob,and keep the private key to her own.
Encryption
Alice gives her public key (n,e) to Bob and keeps the private key secret. Bob then wishes to send message M to Alice. Bob knows the key (n,e). He first turns M into an integer 0 < m < n by using an agreed-upon reversible protocol known as a padding scheme. He then computes the cipher text c corresponding to Unicode, and he links all the numbers from Unicode to a series of number. If the number is long enough, he can put it into several parts, and translate each part to be n. Using the following formula, he can encrpt n to c
Decryption
When Alice gets Bob's message c, she can use her private key d to decrypt the message. She can use the following message to decrpt c to n:
- c^d=n
When she gets’n,She can decrypt the message m to its original text。
The math principle of decryption is
- c^d=n^e
and when ed ≡ 1 (mod p-1)anded ≡ 1 (mod q-1)。This is Fermat's Little Theoremproves [10]
Computer Virus
Definition
A computer virus is a malicious program that replicates itself and invades a computer without the permission of the owner. A computer virus is different than malware, adware, and spyware because they do not have the ability to produce copies of itself. A virus is capable of corrupting or deleting data on your computer and its spread most commonly through e-mail and instant messaging. People commonly attach viruses to executable files that may be part of legitimate programs. This is why viruses pose such a great threat because people open these files and are unaware of the virus being uploaded to their computer. Viruses also can be spread through the internet disguised as attachments such as greeting cards, audio or video files. Some viruses are also very hard to detect and prevent even with the use of anti-virus programs such as Norton. Viruses can be categorized into two types based on their behavior when they are executed. They are Nonresident viruses and resident viruses. Nonresident viruses have two components which consist of a finder module and replication module. A finder module is responsible to search for the executable files to infect then tells the replication module to infect that file. Resident files are subdivided into a category of fast infectors and slow infectors. Fast infectors are primarily designed to infect as many files as possible, whereas slow infectors are designed infect hosts infrequently. They try to avoid detection by limiting their actions by slowing down a computer unnoticeably, and infrequently trigger anti-virus programs software by making it appear less suspicious.
How to prevent getting viruses
To help avoid viruses, try to keep your computer current with the latest updates and antivirus tools, because viruses can be modified and new viruses can be introduced. Viruses can be prevented through anti-virus programs such as Norton; however, viruses can still leak through because viruses are constantly modified to avoid detection. This is why professionals recommend to keep an update on your anti-virus software to prevent this situation. Also another way to prevent viruses is the use of a firewall. Firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
Computer Hacking
What is it?
Computer hacking is a process where an individual(s) modify computer hardware and software to gain access to crucial information or alter a computer’s method of computing. People who engage in computer hacking are known as “hackers.”
Who does it?
Computer hacking is most common among teenagers and young adults, as they have the most knowledge about computers. However, anyone can become a hacker if they have studied computers. Many Computer hackers are self-taught, which means they have a their own unique ways of getting inside computers, which is the reason many high profile institutions, companies, corporations, etc. employ hackers once they have been discovered to find flaws and gaps in their security systems. This helps prevent identity theft, major disruptions, loss of assets, and other serous computer related crimes.
Why do they do it?
Many hackers are “technology buffs” who are very interested in how computers work and how to alter their computing methods. Most hackers are experts in a certain computer program and its programming, and consider it an “art form” rather than a crime. The stereotypical hacker is seen as a teenager locked away in his room all night, trying to gain access to high profile institutions and companies in an attempt to harm them. However, today there are many women hackers, although males still outnumber them. Hackers do not hack into computer systems with the intention of harm, but rather to see how far they can go and what they can accomplish without being discovered.
What about “Cracking”?
In comparison to people who are just curious about computers, people who engage in fraudulent acts such as altering a corportion’s financial data, gaining access to personal data, breaking security codes to gain unauthorized network access, etc. are called “crackers.” This is a serious offense and can earn an offender up to 20 years of jail time.
How can I prevent hackers and crackers from accessing my computer?
There are several ways in which you can protect your computer from hackers and crackers, including arming your computer with the latest anti-virus program, investing in a good firewall, and maintaining updates on your software programs.
High Profile Computer Hackers and Crackers
Discoveries of computer hackers can lead to advancements in security, as will as other technological advancements. For example, former hackers Dennis Ritchie and Ken Thompson created the UNIX operating system in the 1970s, which went on to greatly influence the development of Linux. Another famous computer hacker is Jonathan James, who became the first juvenile at the age of 16 to receive a jail sentence for hacking. James intruded into several high profile organizations. He hacked into a Defense Threat Reduction Agency server, which is an agency of the Department of Defense of the U.S. in charge of reducing threats to the U.S. and its allies from nuclear, biological, chemical and conventional weapons. By gaining access, James was able to view crucial information, emails and employee usernames and passwords. James also hacked into NASA, stealing software estimated at $1.7 million. NASA was ultimately forced to shut down its computer system, because the stolen software was responsible for the physical environment in the International Space Station.
Conclusion
Despite the shortcomings, the Internet carries a wealth of information that is and will continue to be a vital asset for all users. By no means do we advocate the total boycott and avoidance of such a versatile tool. What we do advocate is the greater awareness and understanding of some of the dangers associated with the Internet, so that you may use it with greater confidence and less susceptibility to exploitation. If we have succeeded in such for even a handful of people, we feel that we have accomplished our mission. This is the IT Cops, signing off!
Sources
Identity Theft
- http://www.publicsafety.gc.ca/prg/le/bs/consumers-eng.aspx
- http://canada.justice.gc.ca/eng/news-nouv/nr-cp/2007/doc_32179.html
- http://www.phonebusters.com/english/documents/MonthlyStats_000.pdf
Phishing and Spear Phishing (Chris Chung)
- http://www.microsoft.com/protect/yourself/phishing/identify.mspx
- http://www.webopedia.com/TERM/p/phishing.html
- http://www.webopedia.com/DidYouKnow/Internet/2005/phishing.asp
- http://www.technicalinfo.net/papers/Phishing.html
Chat rooms (Tenzin Dratsangshema)
- http://www.newswire.ca/en/releases/archive/February2007/07/c5906.html
- http://www.id-protect.co.uk/news.php?news_id=50
- http://www.usask.ca/campussafety/personal-safety/id-theft.php
- http://www.webopedia.com/DidYouKnow/Internet/2006/identity_theft.asp
- http://www.identitytheftfixes.com/can_online_chatting_lead_to_identity_theft.html
- http://www.bewebaware.ca/english/aboutus.aspx
- http://disabled-world.com/communication/chat-safety.php
- http://www.rcmp.grc.gc.ca/mb/webpages/internet_e.htm
- http://www.rcmp-grc.gc.ca/ncecc-cncee/factsheets-fichesdocu/chat-clavardage-eng.htm
- http://www.publicsafety.gc.ca/prg/le/bs/report-en.asp
RSA
- http://en.wikipedia.org/wiki/Ron_Rivest
- http://en.wikipedia.org/wiki/Adi_Shamir
- http://en.wikipedia.org/wiki/Leonard_Adleman
- http://en.wikipedia.org/wiki/Clifford_Cocks
- http://en.wikipedia.org/wiki/Prime_number
- http://en.wikipedia.org/wiki/Proofs_of_Fermat%27s_little_theorem
Computer Virus (Kevin Feng)
- http://www.microsoft.com/protect/computer/basics/virus.mspx
- http://en.wikipedia.org/wiki/Computer_virus
- http://vmyths.com/
Computer Hacking
- http://www.wisegeek.com/what-is-computer-hacking.htm
- http://www.hackingalert.com/hacking-articles/hacking-and-cracking.php
Picture sources:
Logo component sources (logo by Chris Chung)
- http://www.sxc.hu/photo/694301
- http://prisonbroadcasting.net/pg/main.htm
- http://movieimage.tripod.com/matrix/slideshowa.html
- http://www.fotosearch.com/UNC323/u12241763/
Phishing pictures
- http://www.volstate.net/phishing.html
- http://www.webopedia.com/DidYouKnow/Internet/2005/phishing.asp
- http://www.nytimes.com/2005/12/04/business/yourmoney/04spear.html
Chat Rooms pictures
- http://www.dengielocal.co.uk/internet-a-computing/94-security/453-chat-room-safety.html
- http://www.bewebaware.ca/english/aboutus.aspx
- http://www.the-best-business.biz/?page_id=2
- http://www.funkydragon.org/en/fe/page.asp?n1=8&n2=1764&n3=1645&n4=1646
RSA pictures
- http://www.usc.edu/dept/molecular-science/pictures/ (click on link that says RSA-2003.jpg)
- http://www.ulm.ccc.de/old/chaos-seminar/krypto2/krypto_bilder.html
Computer Virus picture
Computer Hacking picture