Courses/Computer Science/CPSC 203/CPSC 203 2007Fall L04/CPSC 203 2007Fall L04 TermProjects/I Spy Spyware
Contents
Group Name
Cyber Spies
Group Members
David Hoang, Andrew Gilbert, Riley Fairbanks, Kathy Do, Lee Hong
Project Title
I Spy Spyware
Initial Project Statement
Everyone has heard of the term "Spyware", but what is it? We will explore the purpose, implications, and consequences of spyware. We will be looking at a popular form of spyware called "Internet Optimizer". We will show that spyware is not only an inconvenience, but also an invasion of privacy.
Background of Spyware
What is Spyware?
- Spyware is a branch of Malware - software designed to infiltrate or damage a computer system without the owner's informed consent
- Spyware is software that is installed on the user's computer without the user's explicit consent
- Some forms of Spyware monitor the user's behaviour and collects the user's personal information
- Other forms of Spyware may display unwanted advertisements to the user
- There are a number of ways Spyware may be installed on a user's computer, without the user's knowledge
Brief History of Spyware
Spyware was created off the idea of cookies. Cookies are one of the most important developments in online information collection. Cookies are text files placed on a user's hard drive by a particular website or group of related websites. Originally created to allow user-specific customizations of the internet browsing experience. Often store user preferences, login and registration information or information related to an online "shopping cart". Cookies also contain unique identifiers that allow a website to differentiate among users. Gradually, websites started using cookies for advertising purposes. Website places cookie on user's computer hard drive, and then cookie collects data about consumer's use of that particular site. However cookies are "domain-specific" they can only collect data from browsing on pages within a particular website. For instance amazon.com could place a cookie on a consumer's hard drive, but can only collect data about the consumer's activity within pages on amazon.com. Eventually, advertisers sought to overcome the domain-specific limitations of cookies and developed a means by which they could follow consumers whereever they went on the internet. This was how spyware was created.
How Spyware Works
Spyware is usually installed unknowingly by the user through deception of the user. The user may be completely unaware that he or she is about to install Spyware when the user installs a software package that is bundled with Spyware, or when the user browses a web page and agrees to add functionality to your Web browser. There are four general ways Spyware is installed on the user's computer:
- Piggybacked software installation - Some software will come bundled with Spyware and will automatically be installed on the user's computer when the user tries to install the software package. Often times if the user is not careful to read the installation instructions, Spyware will be installed. The software bundles that come with Spyware are usually free, distributed through the internet and advertised as something useful such as a "download accelerator" or "computer tune-up".
- Drive-by download - This is when the user visits a website and Spyware automatically tries to install itself. The internet browser may ask the user if it's okay to install the software.
- Browser add-ons - Pieces of software that are disguised as something that may help the user by adding toolbars or search boxes to the internet browser, but are bundled with spyware.
- Masquerading as anti-spyware - Software that disguises itself as a anti-spyware solution to the user, but is really Spyware itself.
Spyware, when installed, is at the very least using the user's RAM and processing power, making the user's computer feel sluggish. It may generate many annoying pop-ups that slow down the internet browser, reset the user's homepage to display advertisements, or redirects the user's web searches. Another way Spyware works is to redirect users to "item pages" from major shopping sites such as Amazon.com and eBay, where the Spyware creator receives credit when the user buys items. Certain types of Spyware can modify your Internet settings so that if you connect through dial-up, your modem dials out to expensive, pay telephone numbers.
Spyware - Internet Optimizer
Background
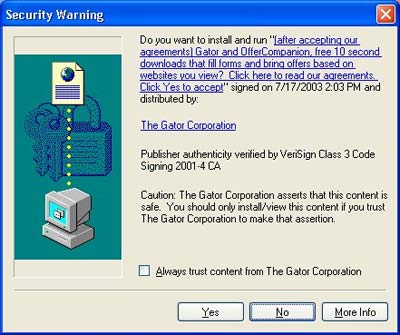
"Internet Optimizer" also known as DyFuCA is an adware and in some applications malware. It was created by a Avenue Media a caribbean based company. The most common form of internet optimizer is refered to as an error page hijacker. Working through the web browser Internet Explorer Internet Optimizer "hijacks" error pages including erroneous URL addresses, broken links, and even password protected sites and sends them to advertising pages controlled by Internet Optimizer's own server. Internet Optimizer is often bundled or accompanied by Money Tree, another spywware classified as a dialer which changes the dial up number from you internet service provider to expensive international 900 numbers.
How did it get on my computer!
While it has been noted that there a several variants of Internet Optimzer and DyFuCA applications the main one is usually aquired when users are invited to follow a link to watch a homourous video. One such video that has been associated with Internet Optimzer is the video of Bill Gates by pied in the face. Once the user has followed the link they are invited to download an application the will "optimize their internet" or improve internet performance. The normal window for downloading appears similar to the example shown above. To complete the download, the user has to agree to Avenue Media's end-user license agreement (EULA). The EULA stipulates four main features that allow the application to work and spread:
- Access to email contacts - The agreement stipulates that Avenue Media may access your email and MSN contacts and send them the same video link, endorsed by the user that the user followed to get internet optimizer thus propigating itself.
- Updates and downloads - The agreement also says that by accepting the agreement the user agree to allow Internet Optimizer to update itself and install new programs as "necessary". This allows other forms of spyware included changes to the original to keep accessing the users computer easily.
- Browsing details - Another section states the Internet Optimizer may send the users browsing information and details back to Avenue Media. This information is then used for advertising purposes.
But I have an anti-virus program that detects spyware!
The way Internet Optimizer is contructed it is classified as a "Browser Help Object" (BHO) which is an application which aids the functioning of a users browser. Many legitimate BHO's exist however Internet Optimizer takes advantage of this which means that it will open and begin functioning everytime the user opens the browser. Also because this application appears legitimate to the user's computer it is often undetected by anti-virus and anti-spyware programs.
Summary
Unfortuneately Internet Optimizer takes advantage of the fact that very few people read the legal details of applications they are downloading. As a result Internet Optimizer is rather controvertial considering the user actually consents to the details of the application. Others however argue that it is an invasion of privacy considering the company clearly takes advantage of the fact that very few people read EULA's. Furthermore that this does not give companies the right to download programs and collect browsing information from users.
How to Protect Yourself from Spyware
Anti-Spyware Programs
There are many programs designed to protect users against spyware. These programs work by watching all the sites visited by an internet user and monitoring them to ensure safe surfing.
Security Practices
There are better ways to protect your computer than simply using an anti-spyware program whenever your computer is acting up. To keep your computer running as smoothly as possible there are many steps you could follow to protect your computer from any serious damages from Spyware.
- Turn on Firewall - It is important to turn on your firewall. This prevents any hackers from directly placing Spyware onto your computer.The firewall monitors the network traffic that is entering and leaving the computer. It permits the safe traffic to enter and prevents inappropriate traffic from entering.
- Anti-Spyware and Anti-Virus - It is also beneficial to download and install anti-spyware programs and anti-virus programs. To increase the protection for your computer, you should install more than just one anti-spyware program. Some programs miss certain Spyware, however with more than one program scanning your computer, this allows the second program to locate any Spyware that was previously missed.
- Keep Updated - It is very important to update the anti-spyware programs. New Spyware are popping up in the internet all the time, and the anti-spyware programs are constantly trying to create updates for the programs to be able to identify and remove the Spywares. Therefore when you update your Spyware program this makes you less vulnerable to the newer Spyware.
- Be Responsible - Being responsible means being more careful when on the internet. Make sure you surf safely on the internet. This means not opening random emails from people you don't know , downloading files from any site, and clicking on any advertising links in pop-up windows.
The Future of Spyware
What is being Done?
Microsoft windows XP and Vista are the most widely used operating systems in the world, which also makes them the most frequently attacked programs as well. Microsoft has developed methods of fighting spyware from infecting its users computers with downloads from the Microsoft website which, are designed to prevent spyware from gaining access to a computer. Internet Explorer is equipped with a pop-up blocker that effectively blocks out many malicious threats to a user. Another program is the Windows Defender which checks a computer for programs that have behave like malicious spyware software and takes actions to eliminate these threats.
Consumer Education
Educating the internet using population is a very important aspect of spyware protection because if people know what will harm their computers then they will be much more careful about their internet use. There are many blogs and discussion boards online that discuss virus and spyware prevention as well as teach others how to keep their computers spyware free. Promoting the use of firewalls is another way in which internet service providers and others provide very useful aid to customers.
Safer Internet Browsers
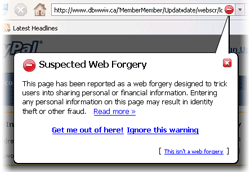
New, safer internet browsers have entered the market and have some major improvements over the Netscape Navigator, Safari and Internet Explorer. The most popular of these is Mozilla's Firefox which effectively eliminates most, if not all spyware threats encountered on the internet and informs the user if a page is not safe and provides all this with an easy to use interface making internet surfing easier. We Expect many more programs like this to be released soon, improving on the already existant spyware blocking software and browsers.
Evolving Spyware
Of course this is a fight that won't be over anytime in the near future because there are improvements being made not only by the "good guys" but also by those who wish to infect a computer with spyware and the newest forms of spyware are harder and harder to combat. However there have been studies conducted which show that over 90% of internet users have changed their browsing habits to avoid spyware contamination which is a good sign for future security. Spyware will also become more geared towards Macs as their popularity increases as will the people who wish to exploit them.
Conclusion
Internet Optimizer is particularly inconvienient considering it is not illegal. Internet Optimizer takes advantage of the fact that users rarely read EULA's and despite the fact that Avenue Media is not breaking any laws, they are invading users privacy and computers. Due to this, little can be done to reduce the amount of spyware on the internet, and each individual must take steps to safe guard themselves from the effects of spyware. Despite not being illegal, spyware in inconvienient, and is often an invasion of privacy. In the future steps need to be taken to protect the privacy of users through legal means.
References
- Background of Spyware
- Anti-Spyware Software:
- General Spyware Information:
- Information on the Spyware "Internet Optimizer":
- Security Practices:
- The Future of Spyware:
- microsoft.com - Microsoft's Spyware Strategy
- spychecker.com - What is Spyware and Adware
- besttechie.net - The future of Malware and Spyware
- computerworld.com - Mutating spyware and the future of spyware technology
- Mozilla.com - Firefox browser and it's features
- news.com - The future of malware
- defeatspyware.org - The Future of Spyware
- consumeraffairs.com What is being done?
- zdnet-adware cannibals
- The Bad Guys-Pop up Ad Companies: